Author: Denis Avetisyan
A new system leverages publicly available data and transparent scoring to detect potentially manipulative activity in financial markets.
This paper details AIMM-X, an explainable framework employing multi-source attention signals and time series analysis for enhanced market integrity monitoring.
Detecting market manipulation remains a significant challenge due to the subtlety of anomalous behavior and the opacity of many surveillance systems. This paper introduces ‘An Explainable Market Integrity Monitoring System with Multi-Source Attention Signals and Transparent Scoring’, presenting AIMM-X, a novel framework that combines traditional market microstructure data with publicly available attention signals to identify potentially manipulative activity. The system utilizes transparent thresholding and an interpretable scoring mechanism decomposed into additive components, enabling auditability and facilitating downstream investigation. Could this approach offer a practical complement to existing proprietary surveillance, ultimately enhancing financial market integrity?
The Inevitable Erosion of Market Integrity
The bedrock of robust financial markets is a commitment to fairness and transparency, principles that enable efficient price discovery and foster investor confidence. However, these ideals are perpetually challenged by manipulative activities, ranging from simple insider trading to sophisticated schemes involving collusion and the dissemination of false information. Such practices erode trust, distort market signals, and ultimately harm both individual investors and the broader economy. The inherent complexity of modern financial instruments, coupled with the speed of electronic trading, creates opportunities for manipulation that are increasingly difficult to detect using conventional surveillance techniques. Consequently, maintaining market integrity demands constant vigilance and the development of innovative strategies to counteract these persistent threats, ensuring a level playing field for all participants.
The escalating sophistication of financial markets, coupled with exponential data growth, presents a significant challenge to conventional surveillance techniques. Historically, monitoring relied on identifying obvious instances of fraud or blatant market breaches; however, increasingly subtle and coordinated manipulative strategies now evade these reactive systems. The sheer volume of transactions, order book dynamics, and news feeds overwhelms human analysts and rule-based algorithms alike. Detecting patterns indicative of manipulation requires sifting through petabytes of data, identifying anomalies amidst legitimate trading activity, and accounting for the complex interplay of various market participants – a task for which traditional methods are demonstrably ill-equipped. Consequently, increasingly sophisticated manipulation schemes are going undetected, eroding market trust and potentially destabilizing the financial system.
Maintaining robust market integrity in the modern era demands a fundamental shift from reactive investigations to proactive surveillance. Contemporary financial ecosystems generate immense datasets, exceeding the capacity of traditional, manual review processes; therefore, sophisticated, data-driven techniques are essential. These approaches leverage statistical modeling, machine learning, and anomaly detection algorithms to identify unusual trading patterns or behaviors that may indicate manipulative activity before significant market disruption occurs. By continuously analyzing real-time data streams, systems can flag suspicious transactions, unusual order book dynamics, or coordinated trading strategies, enabling regulators and exchanges to intervene swiftly and maintain a level playing field. This preemptive capability is crucial not only for protecting investors but also for bolstering confidence in the fairness and efficiency of financial markets.
A Framework for Detecting the Subtle Decay
AIMM-X is an open-source framework designed for market integrity monitoring, leveraging freely accessible data sources. The primary data input consists of Open, High, Low, Close, and Volume (OHLCV) data, commonly available from numerous financial exchanges and data providers. This reliance on public data ensures transparency and reproducibility of anomaly detection results. The framework’s open-source nature facilitates community contributions, peer review, and customization for specific market surveillance needs. While OHLCV data forms the core input, AIMM-X is architected to integrate supplementary data streams, enhancing its ability to detect a wider range of manipulative behaviors and unusual market activity.
Window Segmentation within the AIMM-X framework divides continuous market data into discrete, analyzable intervals. These windows, typically defined by fixed time periods or a specified number of transactions, facilitate the calculation of statistical measures for anomaly detection. To prevent erratic window boundary shifts due to minor data fluctuations, AIMM-X incorporates hysteresis. Hysteresis introduces a threshold; a statistically significant deviation must exceed this threshold and persist for a defined duration before a new window is initiated or an existing one extended, thereby stabilizing the analysis and reducing false positives caused by short-term noise.
Statistical Deviation Detection within the AIMM-X framework operates by quantifying the degree to which current price and volume activity diverges from established norms. This is achieved through a ‘Rolling Baseline Estimation’ technique, which calculates a moving average of historical data to establish a dynamic reference point. The difference between current observations and this rolling baseline is then standardized using the Z-Score, calculated as (X - μ) / σ , where X is the current value, μ represents the rolling mean, and σ is the rolling standard deviation. A Z-Score exceeding a predetermined threshold indicates a statistically significant deviation, flagging the observation as anomalous. This method allows AIMM-X to adapt to changing market conditions and identify unusual activity relative to recent historical behavior, rather than fixed, absolute values.
AIMM-X incorporates external ‘Attention Signals’ derived from social media platforms and news sources to supplement traditional price and volume analysis. These signals are processed using Natural Language Processing (NLP) techniques to quantify market sentiment and identify emerging themes relevant to specific assets. The framework aggregates these sentiment scores and integrates them as additional features in the anomaly detection process, allowing AIMM-X to consider information beyond strictly quantitative data. This approach aims to capture potential market manipulation or shifts in investor behavior that might not be immediately apparent from price action alone, providing a more comprehensive assessment of market integrity.
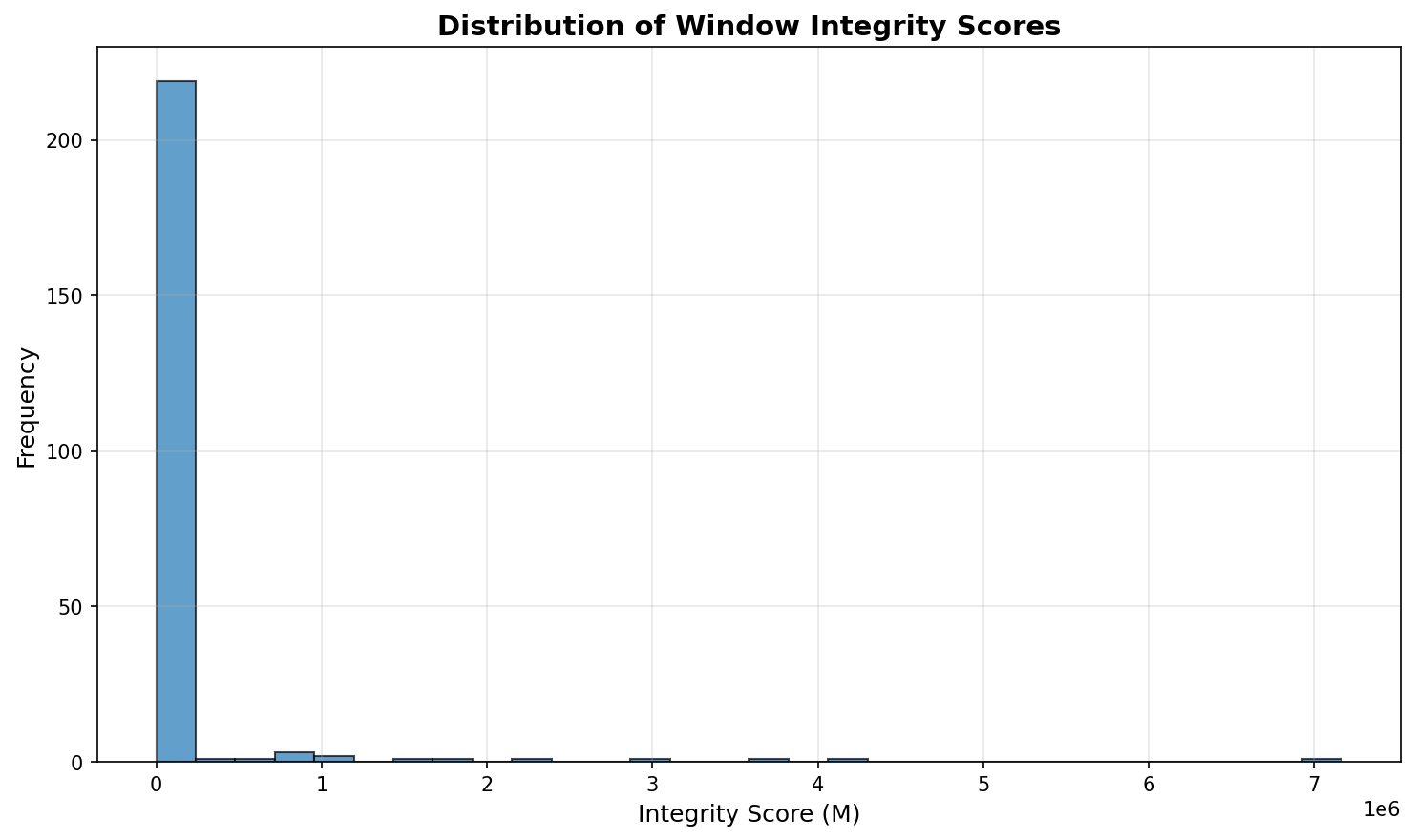
Scoring Anomalies: Quantifying the Rate of Decay
The AIMM-X system generates a ‘Composite Integrity Score’ for each observed ‘Window’ – a discrete time period of trading activity – to prioritize investigation of potentially anomalous behavior. This score is a weighted aggregation of multiple quantitative factors, including but not limited to volume changes, price volatility, order imbalance, and the presence of cancellation waves. Each contributing factor is normalized and scaled to ensure consistent weighting, and the specific weights assigned to each factor are configurable to optimize detection sensitivity based on the asset class and market conditions. Higher Composite Integrity Scores indicate a greater likelihood of manipulative or otherwise suspicious activity within the corresponding Window, allowing analysts to efficiently focus on the most critical instances.
Factor Decomposition within the AIMM-X framework provides granular insight into the Composite Integrity Score by disaggregating it into its contributing components. This allows analysts to move beyond a simple flagged status and directly assess the specific factors driving the anomaly detection. These factors can include, but are not limited to, volume changes, price volatility, order book dynamics, and short-interest ratios. By examining the weighted contribution of each factor, users can validate the alert, identify false positives, and gain a deeper understanding of the underlying market behavior that triggered the flag. The decomposition facilitates a more informed investigation and reduces the time required to determine appropriate action.
Event Calendar Integration within the AIMM-X framework operates by incorporating scheduled corporate events, such as earnings announcements, dividend payments, and stock splits, into the anomaly detection process. This contextualization is achieved by adjusting expected price movements based on historical data surrounding these events; for example, the framework anticipates increased volatility around earnings releases. Anomalies occurring during or immediately following scheduled events are assessed with a reduced severity score, as such fluctuations are considered normal market behavior. Conversely, anomalies occurring outside of these anticipated periods, or exhibiting magnitudes significantly exceeding historical norms even during events, are flagged with higher priority, indicating potentially manipulative or unusual activity. This integration reduces false positives and enhances the accuracy of anomaly detection by differentiating between expected and unexpected price behavior.
Cross-ticker correlation analysis within the AIMM-X framework assesses the relationships between price movements of multiple securities to detect systemic risk and potential manipulative activity. This is achieved by calculating correlation coefficients between the ‘Window’ instances across different tickers; unusually high or synchronized correlations, particularly during periods of low volume or significant price impact, are flagged as potentially anomalous. The system differentiates between naturally correlated securities (e.g., those within the same sector) and those exhibiting statistically significant, unexpected correlations, which may indicate coordinated trading strategies or information leakage. Identified correlations are weighted based on the volume and liquidity of the correlated tickers, and contribute to the overall Composite Integrity Score, providing a quantifiable measure of potential market manipulation or systemic instability.
Validating the Framework: A Necessary Vigilance
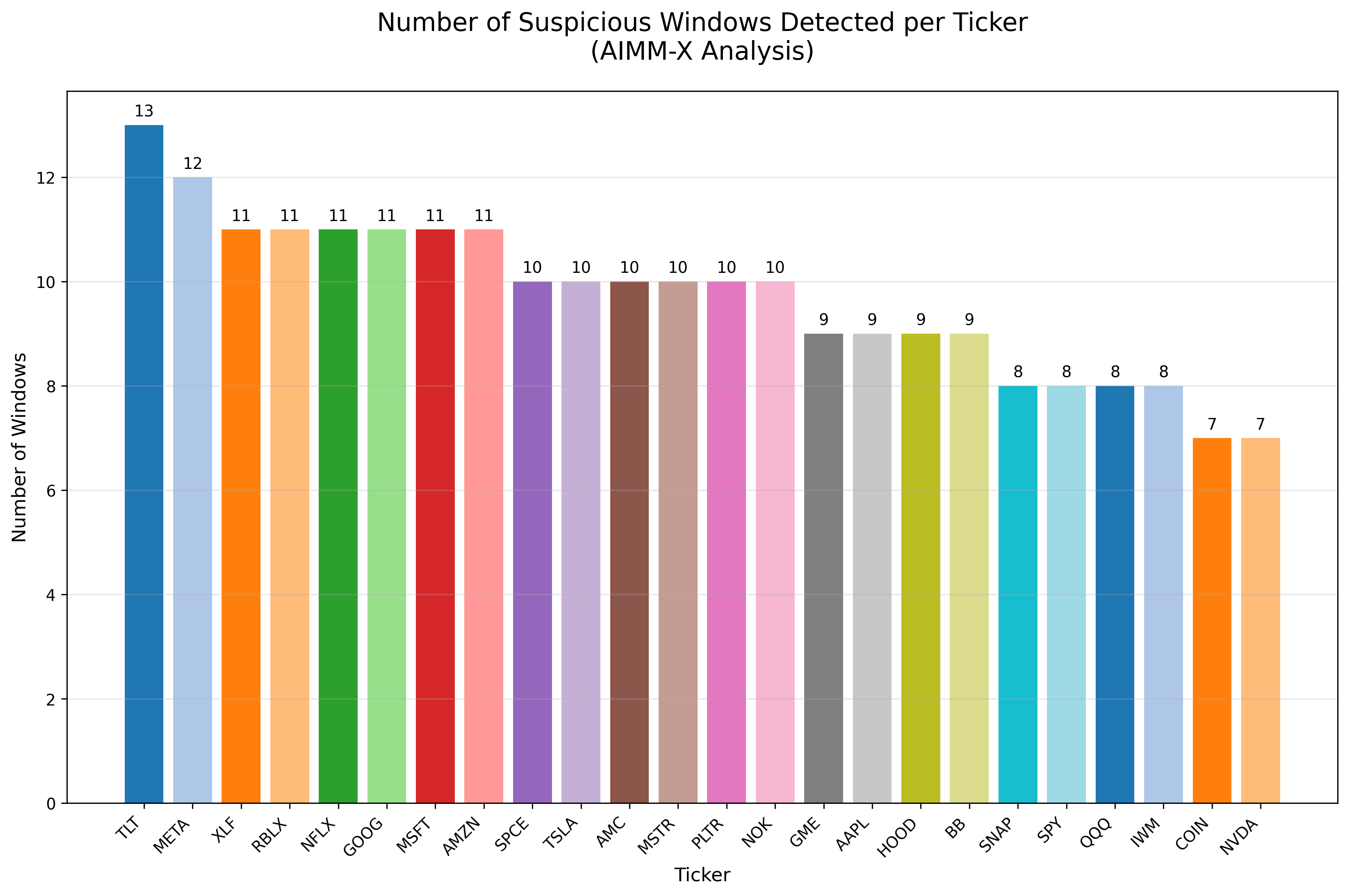
The Automated Insider Monitoring and Modeling – eXplorer (AIMM-X) demonstrated a notable capacity for identifying potentially illicit activity by successfully flagging 233 suspicious trading windows across 24 different securities. This achievement is particularly significant because the system relied solely on publicly accessible data, circumventing the need for costly or difficult-to-obtain private information. Moreover, AIMM-X utilized ‘attention proxies’ – indicators derived from observed data patterns – to pinpoint these anomalies, showcasing its ability to discern subtle, yet potentially critical, behavioral signals within market activity. This initial success establishes AIMM-X as a promising tool for proactively detecting insider trading and other forms of market manipulation, offering a scalable solution for enhanced financial oversight.
The effectiveness of AIMM-X hinges significantly on minimizing its false positive rate – the frequency with which the system incorrectly identifies benign activity as suspicious. A high false positive rate can overwhelm analysts with alerts that ultimately prove unproductive, diminishing trust in the framework and hindering its practical application. Therefore, this metric serves as a crucial benchmark for evaluating AIMM-X’s performance; a lower rate indicates a more refined system capable of accurately distinguishing genuine threats from normal market fluctuations. Continuous monitoring and calibration efforts are thus dedicated to suppressing these erroneous flags, ensuring that analyst workload remains manageable and that the system’s alerts genuinely warrant investigation.
The practical utility of any automated monitoring framework hinges on its ability to minimize false positives – instances where the system incorrectly flags benign activity as suspicious. A high false positive rate quickly overwhelms analysts with irrelevant alerts, negating the benefits of automation and increasing operational costs. Consequently, reducing this rate isn’t merely a matter of improving accuracy; it’s fundamental to ensuring the system remains a viable tool in real-world applications. By streamlining the alert process and focusing analyst attention on genuinely anomalous behavior, a minimized false positive rate directly translates to increased efficiency, reduced workload, and ultimately, a more robust and dependable monitoring capability.
The efficacy of AIMM-X extends beyond initial detection rates, stemming from a deliberately designed system of scoring and interpretation. Unlike ‘black box’ algorithms, AIMM-X provides clear rationales for each flagged instance, detailing which attention proxies contributed most heavily to the overall risk assessment. This transparency is not merely for explanatory purposes; it actively enables continuous improvement. Analysts can readily evaluate the framework’s logic, identify areas where the scoring may be miscalibrated – perhaps overemphasizing certain proxies in specific contexts – and then refine the system accordingly. This iterative process of evaluation and adjustment ensures that AIMM-X remains adaptable to evolving market dynamics and minimizes the potential for false positives, ultimately maximizing its utility as a robust and reliable monitoring tool.
The pursuit of market integrity, as detailed in this framework, isn’t about achieving a static state of ‘correctness,’ but rather a continuous negotiation with entropy. AIMM-X, with its multi-source attention signals, represents an attempt to map the decay inherent in complex systems – financial markets, in this instance – and to understand the vectors of that change. As Michel Foucault observed, “Power is everywhere; not because it embraces everything, but because it comes from everywhere.” This holds true for manipulative practices; they aren’t centralized, but emerge from the interactions within the system itself. The system’s transparency, a core tenet of AIMM-X, isn’t about eliminating power dynamics, but about rendering them visible, allowing for a more informed assessment of the forces at play and delaying the inevitable slide into opacity.
What’s Next?
The introduction of AIMM-X, a system built on publicly available data, represents not an endpoint, but a calibration. Every anomaly detected is, in effect, a moment of truth in the timeline of market behavior. The system’s transparency is valuable, yet transparency itself does not resolve the fundamental tension between detection and the ever-shifting strategies of manipulation. The inherent latency in recognizing manipulative acts will always exist-the question becomes not if they will occur, but when the system’s model begins to reflect the echoes of past offenses, becoming, itself, a predictable target.
Future work must address the inevitable accrual of “technical debt” within the framework. The model’s current reliance on readily available data provides a solid foundation, but also creates a vulnerability. As manipulative actors adapt, the system will require increasingly sophisticated data sources, and with each addition, the promise of full interpretability diminishes. The pursuit of explainable AI, while laudable, carries the risk of becoming a nostalgic ideal, a past mortgage paid by the present’s computational burden.
Ultimately, the longevity of any market integrity system is not measured by its initial accuracy, but by its capacity to degrade gracefully. The system’s value will not be in preventing all manipulation – an impossible task – but in extending the interval between successful offenses, thereby buying time for the market to evolve its own, more resilient, defenses.
Original article: https://arxiv.org/pdf/2601.15304.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Gold Rate Forecast
- Securing the Agent Ecosystem: Detecting Malicious Workflow Patterns
- Silver Rate Forecast
- DOT PREDICTION. DOT cryptocurrency
- 4 Reasons to Buy Interactive Brokers Stock Like There’s No Tomorrow
- NEAR PREDICTION. NEAR cryptocurrency
- EUR UAH PREDICTION
- Did Alan Cumming Reveal Comic-Accurate Costume for AVENGERS: DOOMSDAY?
- Top 15 Insanely Popular Android Games
- USD COP PREDICTION
2026-01-23 08:49