Author: Denis Avetisyan
A new system leverages machine learning and active probing to accurately identify encrypted cryptomining traffic, even when disguised by advanced obfuscation techniques.
CryptoCatch combines traffic classification with XGBoost and active probing to minimize false positives in cryptomining detection.
Despite increasing security risks, detecting illicit cryptomining activity remains challenging due to widespread encryption and high false positive rates of conventional methods. This paper introduces CryptoCatch: Cryptomining Hidden Nowhere, a practical system designed to overcome these limitations through a novel two-stage detection framework. Combining machine learning with active probing, CryptoCatch achieves a 99% F1-score and 99.39% accuracy in identifying specific cryptocurrencies mined over encrypted connections. Can this approach pave the way for more proactive and reliable network security against evolving cryptomining threats?
Unmasking the Silent Harvest: The Rise of Cryptojacking
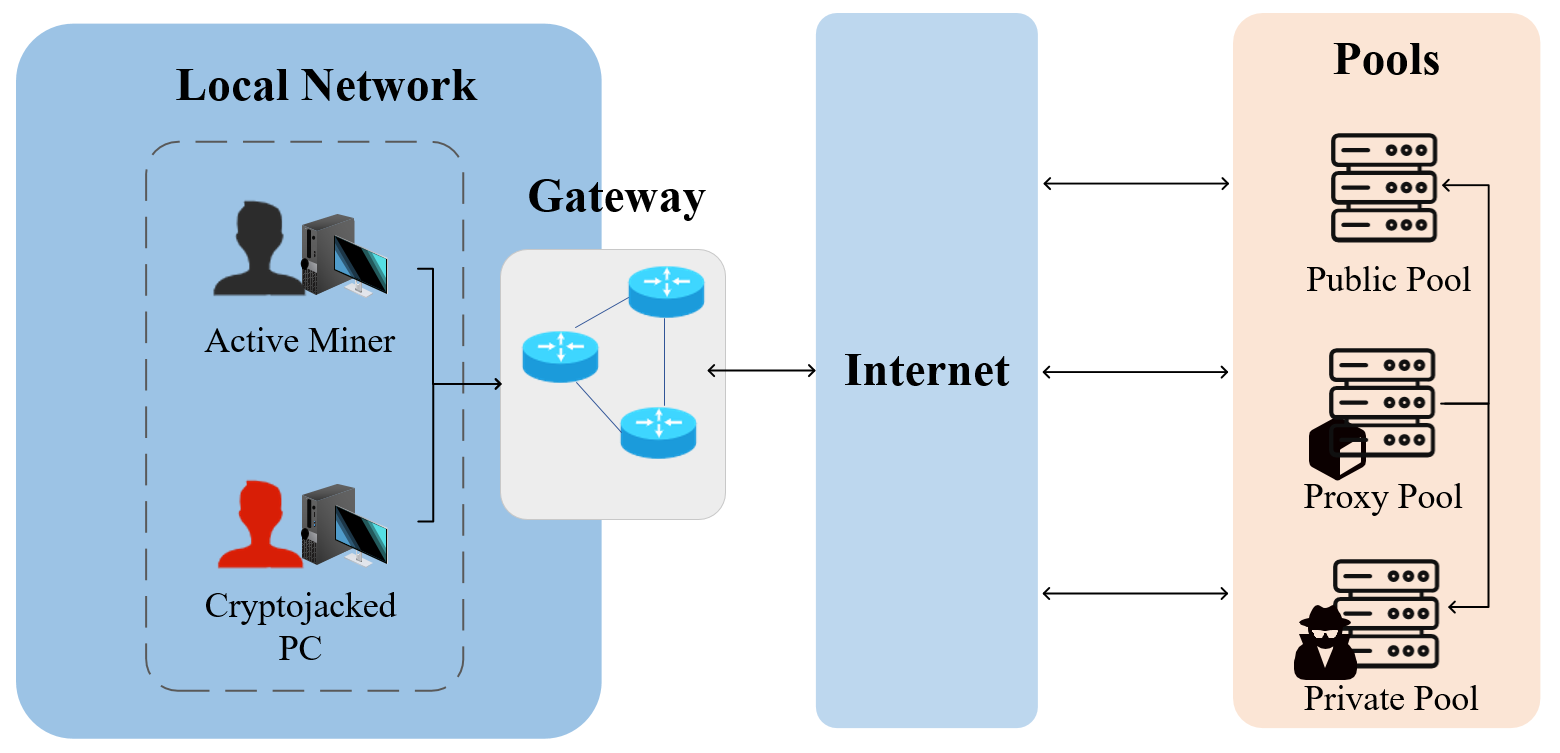
Cryptomining, the process of verifying cryptocurrency transactions and creating new units, operates as a legitimate economic activity, but its underlying mechanics are increasingly leveraged for malicious purposes. This exploitation manifests as cryptojacking, where unauthorized actors commandeer computing resources – from individual laptops and smartphones to large-scale server farms – to mine cryptocurrency without the owner’s knowledge or consent. The fundamental principle remains the same – solving complex computational problems – but the intent shifts from legitimate reward to illicit profit. This parasitic relationship creates a hidden drain on system performance, increases energy consumption, and potentially introduces instability, all while the attacker benefits from the victim’s unknowingly contributed processing power. Consequently, cryptojacking represents a subtle yet pervasive threat, blurring the lines between legitimate network activity and covert exploitation.
Cryptojacking manifests across a diverse threat landscape, extending beyond easily detectable malware. Initial incursions often begin with seemingly innocuous website visits, where malicious JavaScript code embedded within the site hijacks the visitor’s browser to mine cryptocurrency while the page is open – a technique known as drive-by mining. More persistent attacks involve the surreptitious installation of binary files – often disguised as legitimate software or delivered through phishing campaigns – that operate in the background, consuming system resources without the user’s knowledge. These binary infections can be remarkably resilient, employing techniques like rootkits to evade detection and maintain persistence across system reboots. The varied attack vectors and increasing sophistication of these methods present a considerable security challenge, as traditional antivirus solutions struggle to keep pace with the constantly evolving techniques used by malicious actors.
The increasing demand for cryptocurrencies, particularly privacy-focused coins like Monero and those supporting complex smart contracts like Ethereum, directly fuels the rise of cryptojacking. These digital currencies require substantial computational power to generate and validate transactions, creating a financial incentive for malicious actors. Unlike ransomware or data breaches, cryptojacking offers a comparatively subtle and persistent revenue stream; by hijacking processing power, attackers can mine cryptocurrency without directly stealing data or disrupting systems – often going undetected for extended periods. The profitability associated with these currencies, combined with the relative ease of deploying cryptojacking scripts, encourages a continuous influx of new campaigns targeting vulnerable systems and networks, making it a consistently evolving threat landscape.
Detecting cryptojacking presents a unique challenge for cybersecurity systems due to the inherent similarities between authorized cryptocurrency mining and malicious, unauthorized mining. Conventional security tools often rely on identifying the mining process itself, but this approach frequently results in a high number of false positives, flagging legitimate mining operations as threats. This occurs because the core computational activity – solving complex cryptographic puzzles – is identical in both scenarios. Consequently, security teams are inundated with alerts requiring manual investigation, diverting resources and potentially obscuring genuine security incidents. The difficulty in accurately distinguishing between legitimate and malicious mining necessitates the development of more sophisticated detection methods that analyze behavioral patterns, network traffic, and system resource utilization, rather than solely focusing on the mining process itself.
CryptoCatch: A Framework for Dissecting the Hidden Workload
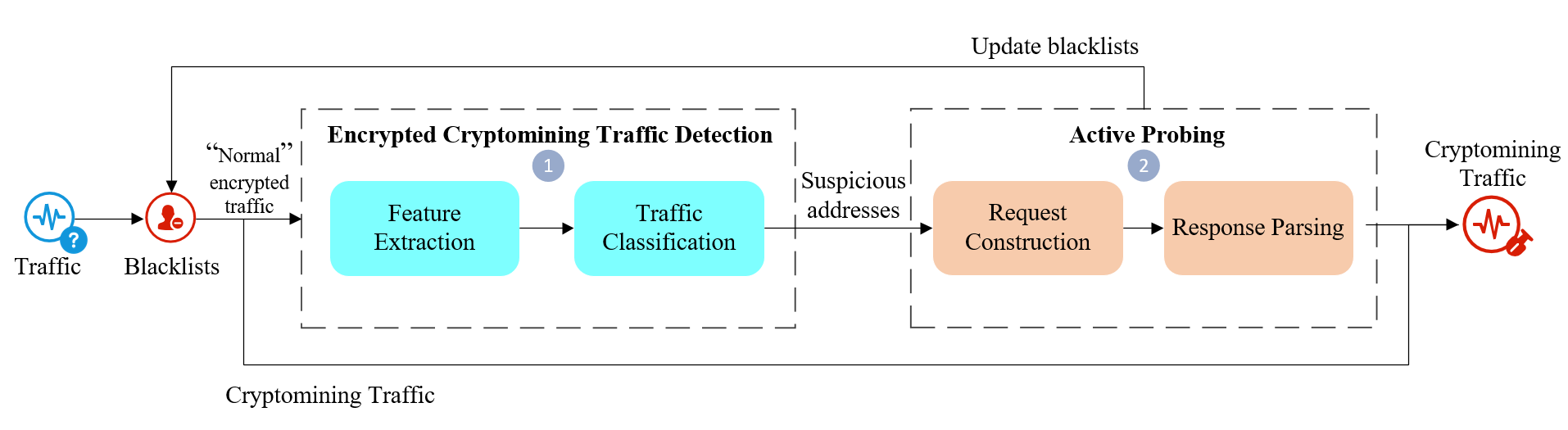
CryptoCatch is a detection framework designed to identify encrypted cryptomining traffic by integrating several analytical methods. Unlike traditional signature-based detection, CryptoCatch doesn’t rely on known malicious domains or patterns. Instead, it utilizes Flow-Level Time Series Classification to analyze network flow characteristics, extracting features indicative of mining activity. This is then combined with Protocol-Specific Active Probing, which interacts directly with mining pools via the Stratum protocol to validate identified destinations. The framework’s multi-faceted approach aims to overcome the obfuscation techniques used by cryptominers and improve detection accuracy, while minimizing false positives through verification of mining pool interactions.
CryptoCatch employs Flow-Level Time Series Classification to analyze network traffic patterns indicative of cryptomining activity. This technique involves extracting a series of Time Series Features from network flows, including inter-packet arrival times, flow duration, packet sizes, and byte frequencies. These features are then used as input to a classification model. By analyzing the temporal characteristics of network flows, CryptoCatch can identify patterns commonly associated with the communication protocols used by cryptominers, such as consistent, periodic communication with mining pools. This approach differs from signature-based detection by focusing on behavioral characteristics rather than known malicious code, enabling detection of novel and obfuscated mining operations.
CryptoCatch employs protocol-specific active probing to validate potential cryptomining destinations identified through flow analysis. This process involves establishing connections with mining pools using the Stratum protocol, the standard communication protocol for most mining operations. By actively interacting with these pools and submitting valid, but benign, work requests, CryptoCatch verifies whether a detected destination is a legitimate and responsive mining server. This verification step distinguishes genuine mining pools from malicious or incorrectly identified network endpoints, contributing to a reduction in false positive detections and ensuring the accuracy of cryptomining traffic identification.
The CryptoCatch framework utilizes XGBoost classification following active probing to achieve a 99.39% accuracy rate in identifying the specific cryptocurrency being mined. This classification step is performed on features derived from protocol-specific interactions with mining pools, allowing for precise identification beyond simple traffic detection. Importantly, this combined approach significantly reduces false positive rates to below 5%, minimizing unnecessary alerts and improving the reliability of the detection system. This performance level was achieved through rigorous testing and validation of the framework’s analytical components.

Refining the Signal: Machine Learning and Active Probing in Concert
The CryptoCatch system utilizes the XGBoost machine learning model for classifying cryptomining activity. To maximize the model’s performance, Bayesian Optimization is employed as a hyperparameter tuning method. This process automatically searches for the optimal combination of XGBoost parameters – including learning rate, tree depth, and regularization terms – by iteratively evaluating model performance with different configurations. Bayesian Optimization uses a probabilistic model to balance exploration of new parameter settings with exploitation of settings already known to yield good results, resulting in a more efficient and effective tuning process than traditional methods like grid search or random search. This fine-tuning is critical for achieving high accuracy and minimizing false positives in cryptomining detection.
Active probing within the CryptoCatch system serves a dual purpose in identifying cryptomining activity. First, it validates the operational status and legitimacy of identified mining pools by directly interacting with them. Second, and crucially, it addresses the challenge of obscured traffic resulting from SSL/TLS encryption. By employing specific probing techniques, CryptoCatch can often bypass or decode encrypted connections, allowing for inspection of network traffic that would otherwise conceal mining-related communications and prevent accurate detection. This circumvention of encryption is vital because a significant portion of cryptomining traffic utilizes SSL/TLS to protect data in transit, effectively hiding its true nature from standard network monitoring tools.
CryptoCatch is engineered to identify cryptomining activity regardless of the operational model employed by the miner. The system analyzes network traffic patterns associated with both individual “solo” miners, who operate independently to solve cryptographic puzzles, and larger, collaborative “mining pools,” where computational resources are combined. This dual-support capability is crucial for comprehensive detection, as miners may dynamically switch between solo and pool mining based on profitability and resource availability. By monitoring for indicators specific to both operational modes, CryptoCatch avoids limitations inherent in systems focused on only one type of mining activity and ensures broader coverage of the threat landscape.
CryptoCatch achieves a demonstrated improvement in cryptomining activity detection, evidenced by an F1-score of 0.99. This metric indicates a high degree of both precision and recall in identifying malicious activity. Crucially, the system maintains a false positive rate below 5%, representing a substantial reduction when contrasted with the industry average of approximately 30%. This minimized false positive rate reduces operational overhead associated with investigating benign events and enhances the reliability of alerts generated by the system.

Beyond the Firewall: Reclaiming Control of the Network
Traditional security measures, such as firewall rules, operate on a passive principle – blocking known malicious traffic or access attempts. CryptoCatch distinguishes itself through an active verification process, going beyond simply permitting or denying connections. The framework analyzes network traffic in real-time, scrutinizing the content for telltale signatures of cryptocurrency mining activity. This proactive stance allows for the identification of cryptojacking attempts, even those leveraging legitimate network connections or employing obfuscation techniques. By verifying the purpose of traffic, rather than solely relying on source or destination, CryptoCatch establishes a more robust defense against an increasingly sophisticated threat, effectively shifting the security paradigm from reactive blocking to continuous validation.
Traditional security measures often react after a cryptojacking attack has begun, attempting to contain damage already inflicted. CryptoCatch, however, fundamentally shifts this paradigm by enabling preemptive intervention. By actively verifying network traffic and identifying malicious cryptocurrency-related communications in real-time, security teams gain the capacity to halt attacks before they establish a foothold. This proactive stance preserves valuable system resources, prevents unauthorized mining operations from consuming bandwidth and processing power, and crucially, avoids the potential for further compromise-effectively neutralizing the threat before it escalates into data breaches or system outages. The ability to anticipate and block these attacks represents a significant advancement in cybersecurity posture, moving beyond simple detection towards genuine prevention.
CryptoCatch distinguishes itself through a deliberately modular architecture, enabling seamless incorporation into pre-existing security ecosystems without necessitating disruptive overhauls. This design prioritizes interoperability, allowing the framework to function alongside established firewall rules, intrusion detection systems, and security information and event management (SIEM) platforms. More critically, the modularity facilitates rapid adaptation to the ever-shifting landscape of cryptojacking threats; as attackers deploy novel techniques or obfuscation methods, individual components can be updated or replaced without affecting the overall system functionality. This future-proof approach ensures continued efficacy and minimizes the time and resources required to maintain robust protection against emerging cryptocurrency-mining malware.
CryptoCatch distinguishes itself through an exceptionally high degree of accuracy in cryptocurrency identification, achieving a 99.39% detection rate that redefines current industry benchmarks. This level of precision isn’t merely about flagging more threats; it dramatically diminishes the burden of false positives on security teams. Traditional systems often generate numerous alerts that require manual investigation, consuming valuable time and resources. By minimizing these spurious signals, CryptoCatch allows analysts to concentrate on genuine threats, optimizing operational efficiency and reducing the overall cost associated with security monitoring. The framework’s reliability translates directly into a more proactive and effective defense against cryptojacking, bolstering an organization’s security posture without increasing the demands on already stretched personnel.
The pursuit of CryptoCatch exemplifies a dedication to understanding system boundaries. This research doesn’t simply accept network traffic as a black box; instead, it actively probes and dissects encrypted streams to reveal hidden cryptomining activity. It echoes Ken Thompson’s sentiment: “Debugging is twice as hard as writing the code in the first place. Therefore, if you write the code first, debug it twice.” CryptoCatch embodies this principle – a meticulous reverse-engineering of network behavior to expose an underlying reality obscured by SSL/TLS encryption. The two-stage approach-machine learning for initial classification, followed by active probing for verification-is essentially an ‘exploit of comprehension,’ systematically testing assumptions to validate findings and minimize false positives. This isn’t merely detection; it’s an intellectual challenge to fully map the system’s vulnerabilities and reveal the truth hidden within.
What’s Next?
The efficacy of CryptoCatch, while promising, ultimately rests on a predictable foundation: pattern recognition. Every exploit starts with a question, not with intent. The system excels at identifying known signatures of cryptomining activity, even when veiled by encryption, but it implicitly concedes ground to truly novel obfuscation. Future work must acknowledge that the adversary isn’t static; adaptation isn’t merely a countermeasure, but an inevitability. The next iteration of detection systems shouldn’t simply react to new techniques, but anticipate them – perhaps by modeling the economic incentives driving obfuscation, or by incorporating game-theoretic principles to predict likely evasion strategies.
A more fundamental challenge lies in the inherent ambiguity of network traffic. Legitimate applications increasingly mimic the behaviors CryptoCatch flags as suspicious – the use of high-bandwidth connections, the establishment of numerous short-lived connections, even the consumption of significant computational resources. Disentangling malicious activity from benign parallelism demands a shift from purely traffic-based analysis to a more holistic understanding of system behavior.
Ultimately, the pursuit of perfect detection is a fool’s errand. The goal isn’t to eliminate false positives entirely, but to minimize the cost of misclassification. A system that correctly identifies 99% of cryptomining activity, but also flags 1% of legitimate traffic as malicious, may be less disruptive – and therefore more effective – than a system with near-perfect accuracy but an unacceptable false positive rate. The true metric isn’t precision, but resilience.
Original article: https://arxiv.org/pdf/2602.10573.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Gold Rate Forecast
- Securing the Agent Ecosystem: Detecting Malicious Workflow Patterns
- Silver Rate Forecast
- DOT PREDICTION. DOT cryptocurrency
- 4 Reasons to Buy Interactive Brokers Stock Like There’s No Tomorrow
- EUR UAH PREDICTION
- NEAR PREDICTION. NEAR cryptocurrency
- Top 15 Insanely Popular Android Games
- Did Alan Cumming Reveal Comic-Accurate Costume for AVENGERS: DOOMSDAY?
- USD COP PREDICTION
2026-02-13 04:45