As a seasoned analyst with over two decades of experience in cybersecurity and blockchain, I’ve seen my fair share of digital bandits and their antics. The resurfacing of the Blockchain Bandit after a five-year hiatus is a chilling reminder of the ever-present threat lurking within the digital frontier.
The Bandit’s return to action is not only a testament to the resilience of this elusive figure but also a stark warning about the importance of security in our increasingly interconnected world. The fact that these particular wallets became active today for the first time since 2018 suggests that the Bandit may have been biding their time, waiting for just the right moment to strike again.
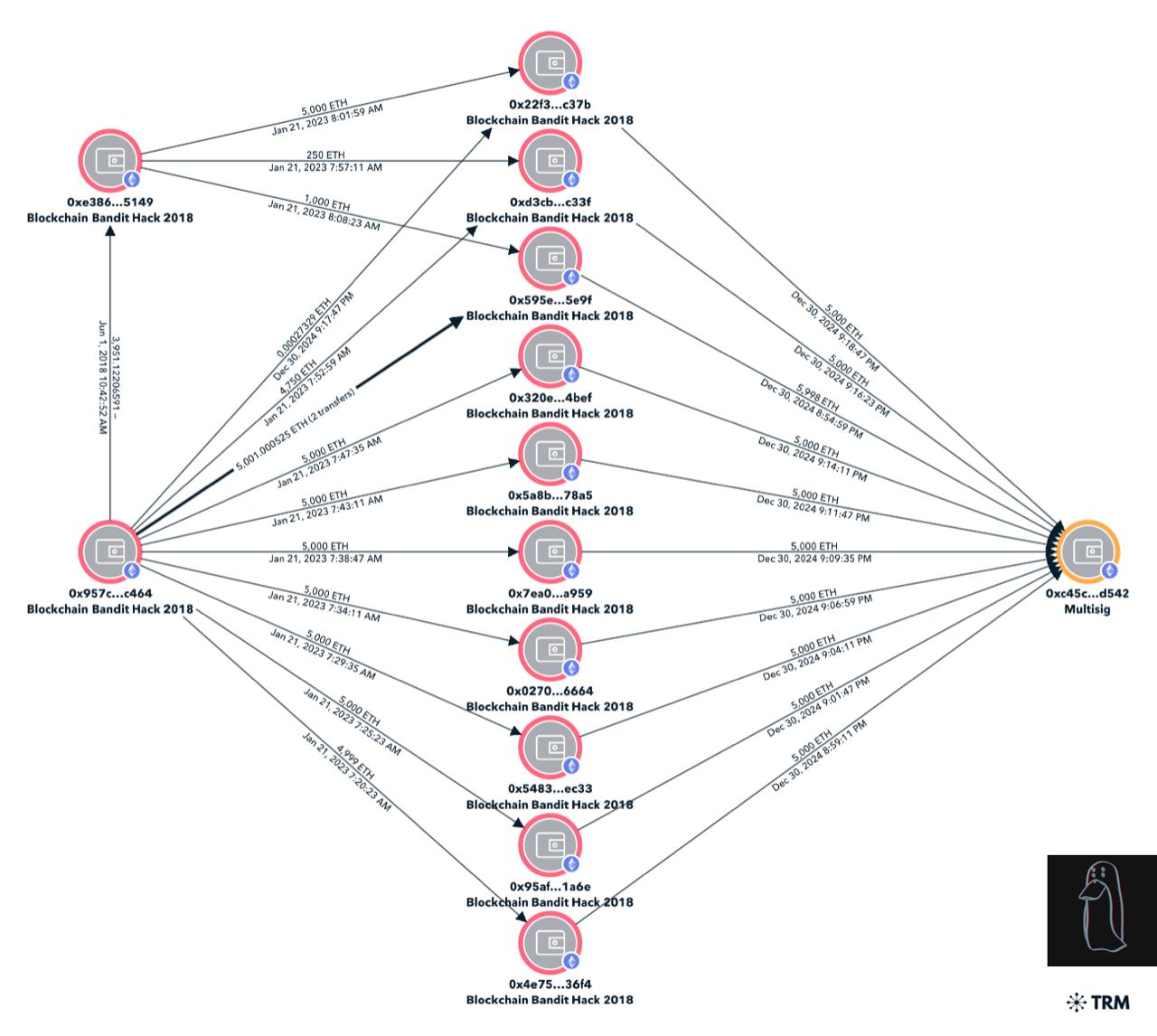
The consolidation of over 51,000 ETH into a multi-sig wallet could be a prelude to several potential scenarios, ranging from laundering activities to further exploits on other blockchain networks. The fact that this attacker was able to amass such wealth by simply guessing weak private keys highlights the importance of using robust security practices in managing digital assets.
In a lighter vein, one might say that the Blockchain Bandit has been hibernating like a bear, only to awaken when the honey (ETH) is ripe for the picking. But remember, this isn’t a fairy tale; it’s a reminder to stay vigilant and secure our digital assets as we continue to explore the boundless frontier of blockchain technology.
It appears that the digital wallets associated with the infamous ‘Blockchain Bandit’ hacker have recently become active following a five-year hiatus. As reported by crypto investigator ZachXBT, this malicious actor moved approximately 51,000 ETH (over $172 million) from ten separate wallets into one multi-signature wallet.
Who is the Blockchain Bandit Hacker?
As a researcher examining the recent blockchain transaction, I found that all ten wallet addresses involved had not been active since 2018. This suggests that the individual controlling these funds has decided to act after more than five years of dormancy.
In the crypto world, this elusive actor is often referred to as the ‘Blockchain Bandit.’ For those who are new to cryptocurrencies, this term might be unfamiliar. However, for long-time enthusiasts, it brings back memories of a captivating and worrying period in 2018.
Known as the “Blockchain Bandit,” this is a term given to an individual who maliciously exploited weak private keys within the Ethereum blockchain, ultimately stealing cryptocurrency. Gaining notoriety by successfully guessing the private keys of numerous vulnerable digital wallets and making off with millions in assets.
An intruder searched the Ethereum network for wallets protected by substandard, predictable, or inadequately created private keys. Frequently, these keys stemmed from software glitches or imperfect usage of cryptographic tools.
The “Blockchain Outlaw” employed computer programs to scan the blockchain network for potentially insecure wallet addresses. Upon discovering a weak encryption key, the hacker swiftly moved funds from the wallet to their own account. Typically, it took several days before the owner noticed the missing funds and realized they had been robbed.
As a seasoned cybersecurity analyst with over a decade of experience, I have seen my fair share of creative methods used by hackers to steal cryptocurrencies. However, the case of the ‘Blockchain Bandit’ stands out as one of the most intriguing and well-executed attacks I’ve encountered. The ability to steal over 50,000 ETH from more than 10,000 wallets using a simple yet sophisticated technique is truly remarkable. It was fascinating to learn about the pre-generated list of keys that allowed the bandit to automate scanning and withdraw funds in seconds. The story of the Blockchain Bandit serves as a reminder that cybercriminals are always finding new ways to exploit vulnerabilities, and it’s essential for us in the security industry to stay one step ahead to protect users and their assets.
In essence, on the Ethereum blockchain, private keys are 256-bit numbers, making it virtually impossible to crack one through brute force. However, some early wallets utilized poor random number generators, leading to weak private keys similar to “password123” or a blank recovery phrase. One key was as simple as ‘1’. The Bandit didn’t merely focus on vulnerable private keys; he also took advantage of weak passphrase-based wallets (like “Brainwallets”) and improperly configured Ethereum nodes. His strategy made him incredibly hard to counteract.
Why is the Attacker Active again After Five years?
Even though some wallets linked to these funds were active as far back as January 2023 and used for Bitcoin purchases, it’s important to note that today marks the first time since 2018 that these specific wallets have become active. Notably, today’s transaction represents the largest consolidation of the stolen ETH funds from the attacker, suggesting potential shifts or strategies in their activities.
Initially, transferring funds into a multi-sig wallet may signal that the potential hacker is getting ready for a significant transaction or multiple transactions. These actions could involve washing the funds by using tumblers, decentralized trading platforms, or other resources to conceal the source of the money.
Additionally, grouping together these funds might signal an intention to sell some or all of the Ether (ETH). It’s worth noting that offloading substantial quantities of ETH in the present market might stir up worries about Ethereum’s immediate pricing trends.
Alternatively, the hacker could predict advantageous market situations, like an increase in Ethereum’s price, to get the most worth from their pilfered assets when they are eventually sold off.
On the other hand, what’s particularly troubling is that the combined ETH might potentially be utilized to fund additional cyber-attacks. This could involve covering transaction fees for a fresh wave of assaults or facilitating activities on other blockchain systems.
As a seasoned cybersecurity professional who has witnessed numerous cyberattacks and their devastating consequences, I can’t help but feel a sense of unease at the prospect of an infamous hacker re-emerging in the crypto space. The industry suffered a staggering loss of $2.3 billion in 2023 alone – a massive 40% increase from the previous year. This alarming trend, coupled with Ethereum being the most targeted network among these attacks, underscores the urgency for stronger security measures to protect both users and investors.
In my experience, I’ve seen firsthand how these attacks can disrupt lives, businesses, and entire communities. The financial losses are just the tip of the iceberg; the damage to trust and confidence in digital assets is immeasurable. It’s crucial that we learn from past mistakes and take proactive steps to fortify our defenses against such threats.
In my opinion, a multi-faceted approach is needed: from educating users on best practices for securing their digital assets, to improving the security infrastructure of networks like Ethereum, to enhancing law enforcement cooperation in cross-border investigations. By working together and taking these measures seriously, we can help ensure a safer, more secure future for the crypto space.
Read More
- 30 Best Couple/Wife Swap Movies You Need to See
- DC: Dark Legion The Bleed & Hypertime Tracker Schedule
- USD ILS PREDICTION
- Clair Obscur: Expedition 33 ending explained – Who should you side with?
- The Last Of Us Season 2 Drops New Trailer: Premiers April On Max
- PENGU PREDICTION. PENGU cryptocurrency
- Everything We Know About DOCTOR WHO Season 2
- Apothecary Diaries Ch.81: Maomao vs Shenmei!
- Tyla’s New Breath Me Music Video Explores the Depths of Romantic Connection
- Save or Doom Solace Keep? The Shocking Choice in Avowed!
2024-12-31 05:36