Picture this: North Korean IT workers laundering a veritable ocean of billions in USDC and USDT, all while donning their best virtual disguises to work as blockchain’s latest and greatest remote employees. Who knew tech startups doubled as the world’s most exclusive front for rogue states? 🌍💻
As North Korea continues its crypto escapade to fund its less-than-charming weaponry programs, the U.S. is ramping up its efforts to snuff out this digital chicanery. On July 8, the Treasury Department slapped sanctions on a hacker named Song Kum Hyok, who allegedly masterminded a scheme involving clueless tech companies entrusting their remote work to the likes of… well, someone who probably shouldn’t have been allowed to operate a toaster, let alone handle sensitive blockchain infrastructure.
Enter TRM Labs, our favorite forensic watchdog, which uncovered that Mr. Song was linked to Andariel—a cybercrime outfit that proudly boasts ties to North Korea’s military intelligence. Sounds like a fun dinner party, right? They report that he played a key role in recruiting so-called IT workers, who were really North Korean operatives living it up in China and Russia, while using the stolen identities of actual Americans. Talk about a plot twist worthy of a Netflix series! 🎬
What were these virtual spies working on? Oh, just your average web3, blockchain, and crypto infrastructure projects—nothing to see here. According to TRM, these operatives were financed with stablecoins, such as USD Coin (USDC) and Tether (USDT), typically employed to provide a sheen of legitimacy to otherwise shady transactions. Much like wearing a tuxedo to a barn dance, really.
“Treasury remains committed to using all available tools to disrupt the Kim regime’s efforts to circumvent sanctions through its digital asset theft, attempted impersonation of Americans, and malicious cyber-attacks.”
— Deputy Secretary of the Treasury, Michael Faulkender
TRM Labs takes us further down the rabbit hole, revealing that the Reconnaissance General Bureau of North Korea—yes, the same ones behind the Lazarus Group—has not given up on the old cyber shenanigans. It’s like watching the villain of a series refuse to admit they’re defeated after three seasons. No amount of economic pressure seems to curb their enthusiasm for crypto theft and identity fraud.
They also casually mentioned that Song was basically a master fabricator of fake identities—think of him as the North Korean Picasso of digital deception. Once these operatives got cozy in their U.S. jobs, sometimes for months or even years, they could really scope out the scene, all under names like “Joshua Palmer” and “Alex Hong.” Who knew tech could sound so suspiciously American? 🇺🇸
To sprinkle some extra intrigue, OFAC sanctioned four companies tied to a Russian network aiding this charade. Bravo! Unsurprisingly, the firms were in on the joke; they just couldn’t resist signing long-term contracts with North Korean-connected companies—because nothing says “trustworthy” like a business agreement with a state department known for hacking. 😏
Cyber Alliance
Meanwhile, the DOJ jumped into action with a civil forfeiture complaint in June, seeking to seize over $7.7 million in crypto and other digital treasures connected to this North Korean circus act. These workers, dressed in their virtual disguises, kept cashing in their crypto, rerouting payouts through various wallets as if it were a twisted game of digital dodgeball.
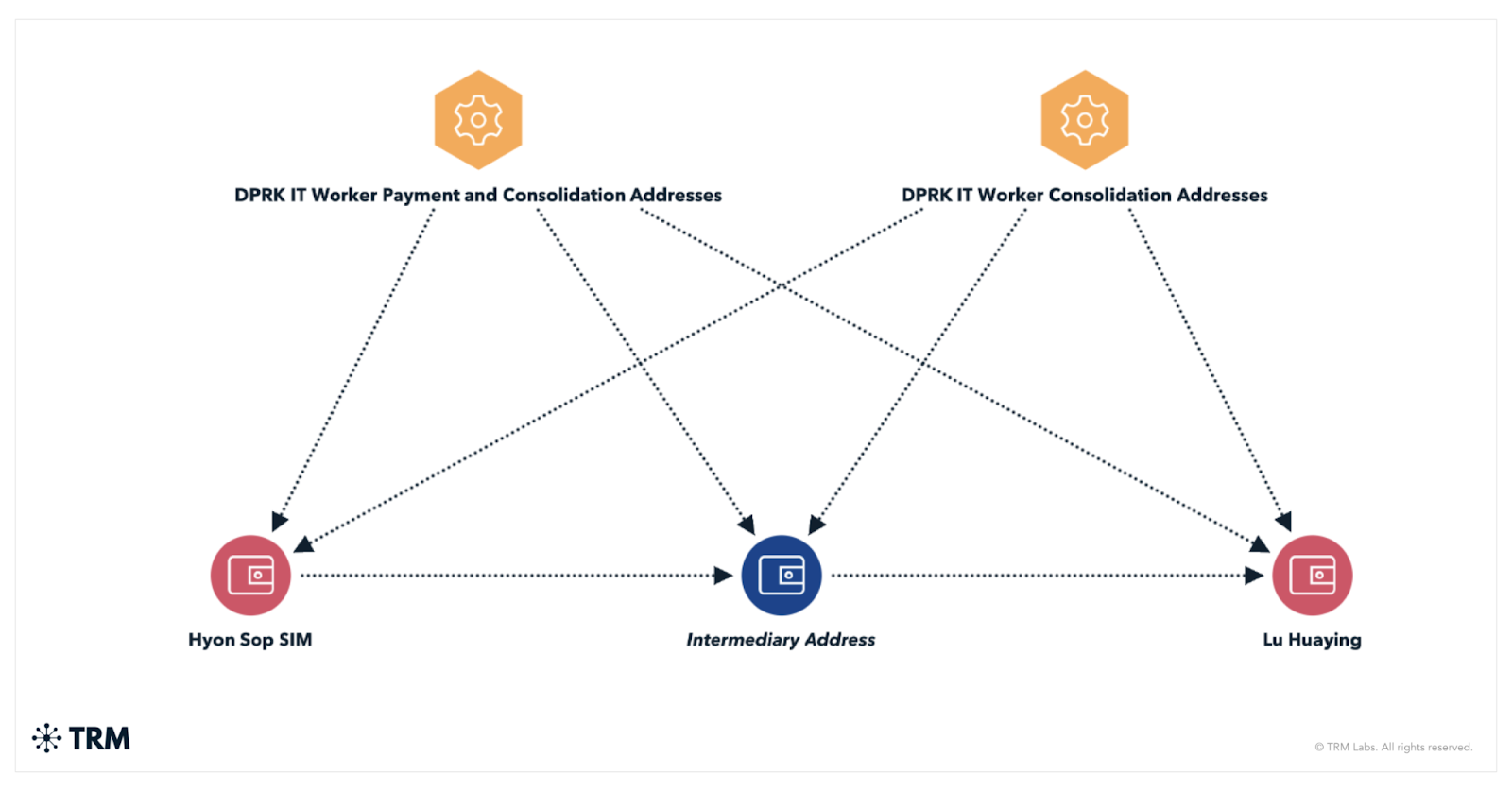
As law enforcement tightened the noose, the FBI managed to grab a slice of the laundered pie, with seizures of USDC, ETH, and those oh-so-valuable NFTs. Here’s to the higher-ups: GitHub surely isn’t ready for a North Korean takeover anytime soon, nor are half of them aware it’s happening! Apparently, the latest hot tip is that any company hiring remote developers should really double-check who’s turning up for the Zoom meetings. Trust me, you’ll thank me later. 🎤
Read More
- Gold Rate Forecast
- 2025 Crypto Wallets: Secure, Smart, and Surprisingly Simple!
- HSR 3.7 story ending explained: What happened to the Chrysos Heirs?
- The 10 Most Beautiful Women in the World for 2026, According to the Golden Ratio
- ETH PREDICTION. ETH cryptocurrency
- Here Are the Best TV Shows to Stream this Weekend on Paramount+, Including ‘48 Hours’
- ‘Zootopia 2’ Wins Over Critics with Strong Reviews and High Rotten Tomatoes Score
- The Best Actors Who Have Played Hamlet, Ranked
- The Labyrinth of Leveraged ETFs: A Direxion Dilemma
- Games That Faced Bans in Countries Over Political Themes
2025-07-16 17:45