Author: Denis Avetisyan
Researchers are leveraging synthetic data and graph autoencoders to uncover hidden relationships in financial transactions and improve anomaly detection.

Graph autoencoders trained on synthetically generated financial data demonstrate effective reconstruction and potential classification of topological patterns associated with illicit activities.
Detecting illicit financial patterns remains challenging due to the scarcity of labeled data and privacy concerns. This limitation motivates the research presented in ‘Synthetic Pattern Generation and Detection of Financial Activities using Graph Autoencoders’, which investigates the utility of Graph Autoencoders (GAEs) for learning and distinguishing topological patterns indicative of money laundering. The study demonstrates that GAEs, trained on synthetically generated transaction data, can effectively reconstruct these patterns, with the GAE-GCN implementation exhibiting the most consistent performance across various illicit activity types. Could this approach pave the way for AI-driven tools capable of proactively identifying financial crime, even in the absence of extensive real-world labeled datasets?
The Inherent Disorder of Illicit Finance
Modern financial crime increasingly relies on obscuring the origins of funds through deliberately complex transaction networks. Traditional fraud detection systems, often built upon predefined rules and static thresholds, prove inadequate against these sophisticated schemes. Criminals exploit the interconnectedness of global finance, layering transactions across multiple accounts and jurisdictions to dismantle the audit trail. This creates a significant challenge, as legitimate financial activity and illicit flows become increasingly indistinguishable. The sheer volume of transactions, combined with the intentional obfuscation, overwhelms rule-based systems, resulting in a high number of false alarms and, critically, allowing substantial amounts of laundered money to evade detection. Consequently, a shift towards analyzing the structure of financial networks, rather than individual transactions, is essential to effectively combat these evolving threats.
The sheer scale of contemporary financial activity presents a formidable challenge to traditional fraud detection. Modern systems, often reliant on predefined rules, are increasingly overwhelmed by the volume and velocity of transactions occurring daily. This constant deluge results in a high incidence of false positives – legitimate transactions flagged as suspicious – diverting valuable resources and obscuring genuine criminal activity. Consequently, sophisticated money laundering schemes are slipping through the cracks, as rule-based systems struggle to differentiate between normal, high-frequency trading and deliberately obscured illicit flows. The inability to process and analyze data at this speed and scale effectively diminishes the efficacy of current methods, creating a critical vulnerability in the global financial system.
Traditional financial fraud detection relies heavily on predefined rules – flagging transactions exceeding certain amounts or originating from specific locations. However, increasingly sophisticated illicit finance schemes deliberately circumvent these simple checks by distributing funds across vast, interconnected networks. Consequently, effective detection now necessitates a shift in focus from individual transactions to the structure of the financial ecosystem itself. Analysts are beginning to explore techniques that model relationships between entities – identifying not just suspicious amounts, but also unusual patterns of connection and information flow. This approach allows for the identification of anomalous network behavior, such as unusually dense clusters of transactions or unexpected paths of funds, which would otherwise remain hidden within the noise of legitimate activity. By understanding how money moves through a system, rather than simply how much money moves, investigators can uncover previously undetectable patterns of criminal finance.
Contemporary financial crime detection relies heavily on systems ill-equipped to handle the intricacies of modern money laundering. These methods often treat transactions as isolated events, failing to recognize the subtle yet crucial relationships that define illicit networks. Consequently, sophisticated criminals exploit this limitation by layering transactions through multiple accounts and jurisdictions, effectively camouflaging the true origin and destination of funds. The inability to model these complex interdependencies creates a substantial vulnerability within the financial system, allowing vast sums of illicit capital to flow undetected and undermining efforts to combat financial crime. This systemic weakness demands a shift towards analytical approaches that prioritize network analysis and relationship discovery, rather than solely focusing on individual transaction characteristics.
Graph Autoencoders: A Structural Decomposition of Financial Flows
Graph Autoencoders (GAEs) operate on the principle of unsupervised learning to generate condensed, vector-based representations – or embeddings – of nodes within a graph. These embeddings capture the structural properties of the transaction network, reflecting relationships between entities and the flow of funds. By learning a lower-dimensional representation of the graph, GAEs can effectively reduce noise and highlight key patterns indicative of normal transactional behavior. Anomalies, representing deviations from these learned patterns, are then detectable as reconstruction errors; the greater the difference between the original graph and its autoencoded reconstruction, the higher the likelihood of fraudulent activity. This approach is particularly effective in financial crime detection because it doesn’t rely on pre-defined fraud signatures, instead identifying unusual patterns based on the network’s inherent structure.
Graph Autoencoders (GAEs) operate on the principle of learning a compressed representation of a transaction network, then reconstructing the original graph from this reduced form. The reconstruction process isn’t expected to be perfect; the magnitude of the difference between the input graph and the reconstructed graph-quantified as a reconstruction error-serves as an anomaly score. Higher reconstruction errors indicate that the GAE struggles to represent a particular node or subgraph based on the learned patterns of normal behavior, suggesting potentially fraudulent activity. This deviation from expected reconstruction is the core mechanism for identifying anomalies within the transaction network, as fraudulent transactions often exhibit structural or feature characteristics that differ significantly from legitimate ones.
Incorporating node properties as input features within Graph Autoencoders (GAEs) significantly improves the model’s ability to differentiate between normal and anomalous transaction behavior. These properties, which can include transaction amount, time intervals, geolocation, or merchant categories, provide crucial contextual information beyond the graph’s structural connectivity. By embedding these features into the node representations learned by the GAE, the model can more accurately capture the nuances of each transaction. This enriched representation enables the detection of subtle anomalies that might be missed when relying solely on graph topology, leading to enhanced fraud detection accuracy and reduced false positive rates.
Adam optimization, utilized during the training of Graph Autoencoders (GAEs) for financial crime detection, is a stochastic gradient descent method that computes adaptive learning rates for each parameter. This is achieved by maintaining both a first moment estimate (mean) and a second moment estimate (uncentered variance) of the gradients. These estimates are then used to normalize the learning rate for each parameter, resulting in faster convergence and improved performance compared to traditional stochastic gradient descent. Specifically, the algorithm incorporates bias correction to compensate for the initial values of the moment estimates, and hyperparameter settings such as learning rate, beta1, and beta2 control the decay rates of these moving averages. This efficient refinement process enables the GAE to accurately capture and represent patterns of normal transaction behavior, forming a baseline for anomaly detection.
Topological Signatures: Dissecting the Geometry of Fraud
Topological patterns represent recurring graph structures indicative of fraudulent behavior in financial networks. These patterns include the Collector Pattern, where funds converge on a single entity; the Sink Pattern, denoting an endpoint for illicit funds with no outflow; the Scatter-Gather Pattern, characterized by funds dispersed and then consolidated; the Cyclic Pattern, indicating repeated transactions between entities; the Branching Pattern, representing funds distributed to multiple destinations; and the Collusion Pattern, signifying coordinated activity between multiple actors. Identification of these patterns allows for focused investigation of potentially fraudulent transactions and entities within a larger financial graph, as they deviate from typical legitimate network behavior.
To address the challenge of limited labeled data for training Graph Autoencoders (GAEs) in fraud detection, a synthetic data generation process was implemented. This process created 15,000 samples for each of the identified topological patterns – including Collector, Sink, Scatter-Gather, Cyclic, Branching, and Collusion patterns. The generated dataset was then partitioned into training and validation sets with an 80/20 split. This data augmentation strategy served to enhance the robustness and performance of the GAE models in accurately identifying these indicative patterns, particularly in scenarios where real-world labeled data is scarce.
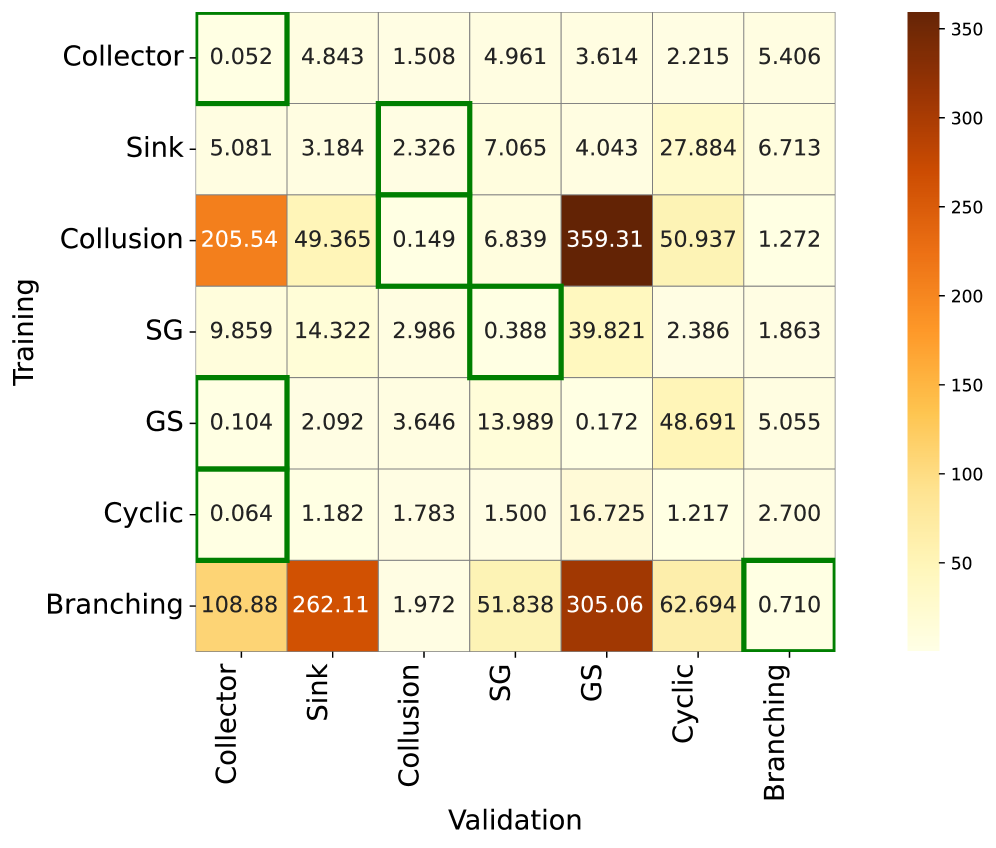
Graph Autoencoder (GAE) performance in identifying topological patterns is quantitatively assessed through Reconstruction Error, which measures the difference between the original graph and the graph reconstructed by the GAE. Lower Reconstruction Error indicates a greater ability of the GAE to accurately learn the underlying graph structure and, consequently, the embedded topological patterns. Analysis, as visualized in Figure 3(a), demonstrates that GAE models employing Graph Convolutional Networks (GAE-GCN) consistently achieved the lowest Reconstruction Errors, indicated by the concentration of green boxes along the diagonal; this suggests superior performance in graph reconstruction and, by extension, accurate detection of the specified patterns.
Implementations of Graph Autoencoders (GAEs) utilizing Graph Convolutional Networks (GCN) and GraphSAGE algorithms demonstrate improved topological pattern detection capabilities. Specifically, the GAE-SAGE model successfully identified patterns in 3 instances, while the GAE-GAT model correctly detected patterns in 4 cases. These advanced GAEs leverage specialized graph processing techniques to more effectively analyze network structures and distinguish between legitimate and fraudulent activity, exceeding the performance of standard GAE implementations by capitalizing on the unique characteristics of each graph-based algorithm.
Beyond Reactive Detection: Towards Proactive Financial Intelligence
Traditional fraud detection often focuses on individual transactions, flagging anomalies in isolation. However, this approach frequently misses sophisticated criminal activity orchestrated through complex networks. This technology shifts the focus to the structure of financial relationships, identifying patterns indicative of illicit behavior even when individual transactions appear legitimate. By mapping connections between accounts and analyzing network topology – things like identifying unusually dense clusters or central nodes with disproportionate influence – it reveals the underlying architecture of criminal financial networks. This allows for a more holistic understanding of how funds are moved and laundered, going beyond simply pinpointing fraudulent acts to uncovering the organizational framework supporting them, ultimately enabling preventative measures and targeted disruption of these networks.
The convergence of Graph Autoencoders (GAEs) and anomaly detection methodologies delivers a powerful capability for dynamic financial surveillance. By learning the typical patterns of financial networks, GAEs establish a baseline for expected transactional behavior. When combined with anomaly detection, deviations from this learned baseline – unusual transaction amounts, frequencies, or network connections – are immediately flagged as potentially suspicious. This integration transcends static fraud detection, enabling real-time monitoring of transactions as they occur and facilitating the proactive identification of illicit financial activity before it fully propagates through the system. The resulting system allows financial institutions to move beyond simply identifying known fraud schemes and instead focus on emerging threats and previously unseen patterns of financial crime.
The incorporation of Graph Attention Networks represents a significant advancement in discerning critical elements within complex financial networks. Unlike traditional graph analysis methods that treat all connections equally, these networks utilize an ‘attention’ mechanism, allowing the system to prioritize the most relevant nodes and edges. This selective focus isn’t arbitrary; the network learns to assign weights based on the influence each connection has on overall network behavior, effectively highlighting pathways crucial to illicit financial flows. By concentrating analytical resources on these high-priority areas, the system achieves demonstrably improved accuracy in identifying suspicious activity, while simultaneously increasing processing efficiency and reducing false positives – a vital combination for real-time monitoring and effective intervention within the global financial landscape.
The deployment of advanced financial intelligence systems promises a shift from reactive fraud investigations to preemptive disruption of illicit financial flows. By analyzing the complex relationships within financial networks, institutions can now identify and neutralize criminal activity before funds are successfully laundered or utilized for illegal purposes. This capability extends beyond simply flagging suspicious transactions; it allows for the targeting of key nodes and the dismantling of entire criminal networks, bolstering the stability and trustworthiness of the global financial system. The result is a more secure environment for legitimate financial activity and a significant impediment to those seeking to exploit the system for unlawful gain, ultimately enhancing the integrity of international commerce and reducing financial crime.
The pursuit of robust anomaly detection, as explored within this research, hinges on the creation of mathematically sound models. This aligns perfectly with Dijkstra’s assertion: “It’s not enough to show that something works; you must prove why it works.” The paper’s use of Graph Autoencoders to reconstruct synthetic financial patterns isn’t simply about achieving high accuracy; it’s about establishing a provable method for identifying topological anomalies. The generation of synthetic data, crucial for overcoming the scarcity of labeled examples, demands a rigorous underlying structure, mirroring Dijkstra’s emphasis on logical completeness. A flawed generative model would inherently propagate errors, rendering the entire system unreliable, irrespective of its performance on test datasets. Therefore, the approach emphasizes verifiable correctness over mere empirical success.
What’s Next?
The demonstrated capacity to generate and detect topological patterns within synthetic financial data, while a necessary step, merely clarifies the fundamental challenge. The reconstruction fidelity of the Graph Autoencoder, impressive as it may be, does not address the axiomatic problem of defining ‘anomaly’. A perfect reconstruction is, after all, a tautology; the interesting cases lie at the boundaries of representational capacity. Future work must rigorously define the topological invariants that constitute fraudulent activity, rather than simply identifying deviations from a learned norm.
A crucial, and often overlooked, limitation is the inherent abstraction of the synthetic data itself. The fidelity of the simulation is, at best, an approximation of the complex, and often irrational, behaviors driving real-world financial transactions. Consequently, the transferability of these models to live data remains an open question. A mathematically sound approach would involve establishing provable bounds on the error introduced by the synthetic data, a task currently lacking in the broader field of anomaly detection.
The pursuit of ‘generalizable’ anomaly detection algorithms, divorced from specific domain knowledge, appears increasingly futile. The true elegance lies not in identifying any deviation, but in precisely characterizing those deviations that violate established economic or legal principles. Therefore, future research should focus on integrating formal methods – theorem proving, model checking – with Graph Autoencoders, to move beyond empirical performance and towards a truly verifiable system.
Original article: https://arxiv.org/pdf/2601.21446.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- 2025 Crypto Wallets: Secure, Smart, and Surprisingly Simple!
- Brown Dust 2 Mirror Wars (PvP) Tier List – July 2025
- Wuchang Fallen Feathers Save File Location on PC
- Gold Rate Forecast
- Gemini’s Execs Vanish Like Ghosts-Crypto’s Latest Drama!
- HSR 3.7 breaks Hidden Passages, so here’s a workaround
- Banks & Shadows: A 2026 Outlook
- QuantumScape: A Speculative Venture
- The 10 Most Beautiful Women in the World for 2026, According to the Golden Ratio
- Solel Partners’ $29.6 Million Bet on First American: A Deep Dive into Housing’s Unseen Forces
2026-01-30 07:22