Author: Denis Avetisyan
A new technique fortifies the privacy of network communities by subtly altering both the connections and characteristics of nodes, making them harder for machine learning models to identify.
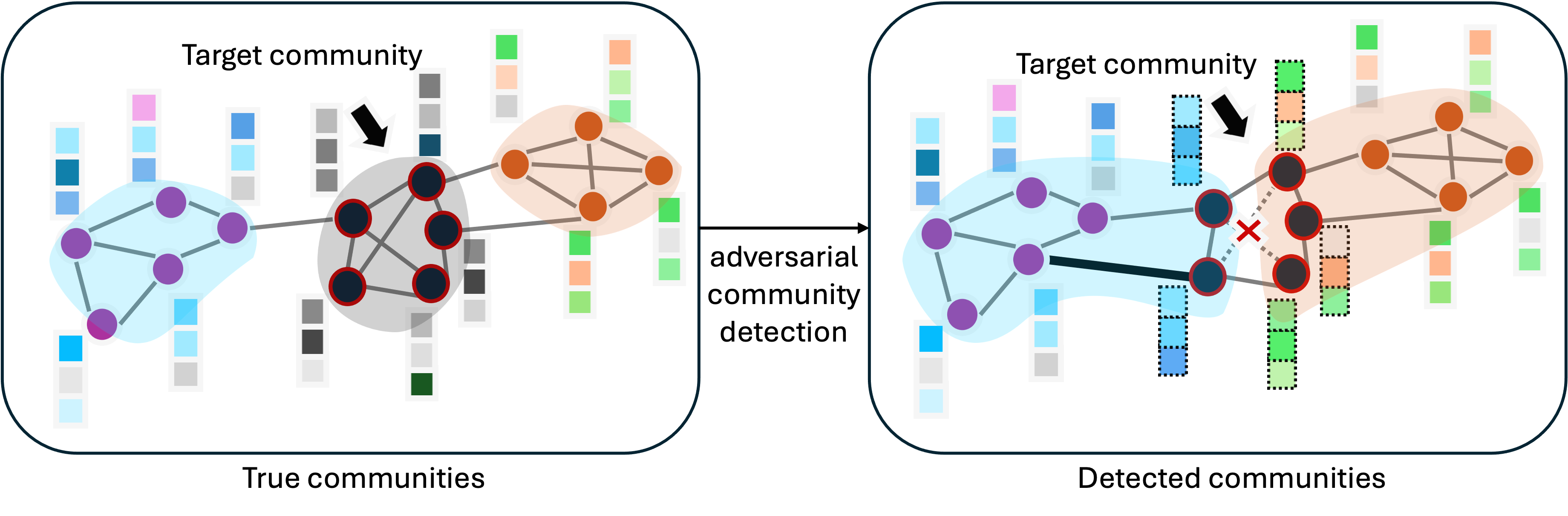
This paper introduces FCom-DICE, a method that improves community concealment in graph neural networks through strategic perturbation of graph structure and node features.
Despite the power of graph neural networks (GNNs) for unsupervised learning and community detection, their application to attributed graphs raises significant group-level privacy concerns by potentially revealing sensitive affiliations and system dependencies. This paper, ‘Community Concealment from Unsupervised Graph Learning-Based Clustering’, addresses this challenge by investigating methods to conceal a target community while minimizing alterations to the underlying network. The authors demonstrate that effective concealment hinges on manipulating both connectivity at community boundaries and feature similarity between groups, leading to a novel perturbation strategy-FCom-DICE-that outperforms existing structural-only approaches by approximately 20-45%. Could this approach provide a foundational strategy for balancing utility and privacy in increasingly interconnected graph-based systems?
The Illusion of Connectivity: Why We Assume We Understand Networks
Understanding the behavior of complex systems – from social networks and the brain to infrastructure and the internet – often hinges on identifying the communities within them. These groupings, where connections are dense internally but sparse externally, reveal functional organization and emergent properties. However, as networks expand in size and intricacy, discerning these communities becomes exponentially more challenging. Traditional algorithms struggle with the sheer volume of data and the subtle, overlapping relationships characteristic of real-world networks. The increasing scale not only demands greater computational resources, but also introduces noise and ambiguity, making it difficult to differentiate genuine community structure from random fluctuations or intentional obfuscation. This growing difficulty threatens the ability to accurately model, predict, and ultimately control the behavior of these vital interconnected systems.
Many established algorithms for identifying communities within networks operate on the premise of predictable patterns – such as dense connections within groups and sparse connections between them. However, this reliance on specific structural assumptions introduces vulnerability; deliberately crafted networks, even subtly altered ones, can easily mislead these methods. An adversary, for example, might add carefully placed links to obscure true community boundaries, or introduce ‘bridge’ nodes that connect disparate groups, effectively camouflaging the underlying organization. Furthermore, real-world networks rarely conform to neat, idealized models; communities can be overlapping, fuzzy, or defined by attributes beyond simple connectivity, posing challenges for algorithms that demand clear-cut groupings. Consequently, the efficacy of traditional community detection techniques diminishes when faced with the complexities of adversarial attacks or the subtleties of nuanced, real-world network structures.
The very challenge of accurately mapping connections within complex networks has spurred a parallel field of research focused on camouflaging those same connections. Researchers are actively developing techniques to deliberately obscure community structures, effectively creating “dark” communities within a network, and these methods aren’t solely defensive. Such adversarial strategies, initially conceived as a means to test the robustness of community detection algorithms, raise significant concerns about network security; malicious actors could utilize these same techniques to conceal harmful activity, like botnet command-and-control or fraudulent transactions. This intentional obfuscation also threatens analytical integrity, potentially invalidating data-driven insights derived from network analysis and demanding the creation of more resilient, and sophisticated, detection methods capable of piercing these carefully constructed veils of concealment.
DICE: A Baseline for Network Disruption
The DICE algorithm functions as a foundational technique for obscuring community structure within a network by selectively altering its edges. Specifically, DICE operates by removing edges that connect nodes within identified communities, effectively disrupting internal cohesion. Simultaneously, the algorithm adds edges between different communities, aiming to connect previously isolated groups and reduce the overall modularity of the network. This process of intra-community edge removal and inter-community edge addition is performed iteratively, guided by a defined ‘PerturbationBudget’ that limits the total number of edges that can be modified. The goal is to create a network topology that appears less structured and more random, hindering the detection of underlying community affiliations through standard network analysis techniques.
The DICE algorithm, while effective at structural perturbation, operates solely on network topology, disregarding node characteristics and associated feature data. This limitation means DICE cannot leverage node attributes – such as demographics, content, or behavioral patterns – to guide edge rewiring, potentially resulting in manipulations that disrupt meaningful community structures beyond simple connectivity. Consequently, rewiring decisions made without considering the feature space may introduce anomalies detectable through attribute-based analysis, or create perturbations that are less effective at concealing the original community structure compared to an approach incorporating feature awareness. The absence of feature consideration also restricts DICE’s ability to minimize perturbation impact, potentially necessitating a larger ‘PerturbationBudget’ to achieve the desired level of community hiding.
The effectiveness of the DICE algorithm is fundamentally limited by the defined ‘PerturbationBudget,’ which dictates the maximum number of edges that can be removed and added during the network manipulation process. This budget represents a trade-off between the degree of community obfuscation achievable and the potential for detection; larger budgets allow for more substantial alterations to the network structure, increasing the difficulty of identifying the original community assignments, but also elevate the risk of statistical anomalies or triggering suspicion. Consequently, a lower perturbation budget may preserve network characteristics and reduce detectability, but may also result in incomplete community hiding. The optimal perturbation budget is therefore context-dependent and requires careful consideration of the network’s size, density, and the sensitivity of the detection mechanisms employed.
FComDICE: Injecting a Little Sense into Network Camouflage
FComDICE extends the functionality of the DICE algorithm by integrating node attributes and a ‘FeatureSpace’ to guide edge modifications. Unlike DICE, which operates solely on network topology, FComDICE considers the inherent characteristics of nodes when rewiring edges. This is achieved by representing each node’s attributes within the FeatureSpace, allowing the algorithm to quantify the similarity between nodes. During edge rewiring, FComDICE prioritizes connecting nodes that exhibit high similarity within this FeatureSpace, effectively leveraging node attributes to create perturbations that are more consistent with expected network behavior and less likely to be detected as anomalous.
FComDICE’s perturbation strategy centers on minimizing feature discrepancies between directly connected nodes during edge rewiring. Rather than random modifications, the algorithm prioritizes establishing connections between nodes possessing similar attribute values within the defined ‘FeatureSpace.’ This approach seeks to create network alterations that appear statistically plausible and less indicative of deliberate manipulation. By preserving feature similarity during edge adjustments, FComDICE aims to reduce the detectability of the perturbation, as changes are more likely to be interpreted as natural variations within the network rather than adversarial interventions.
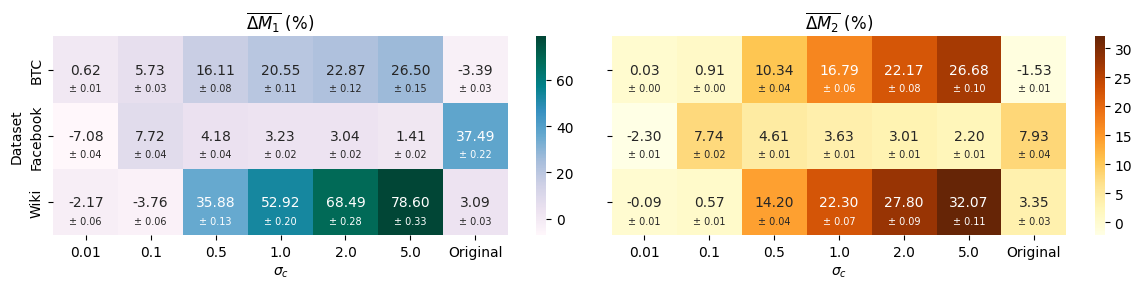
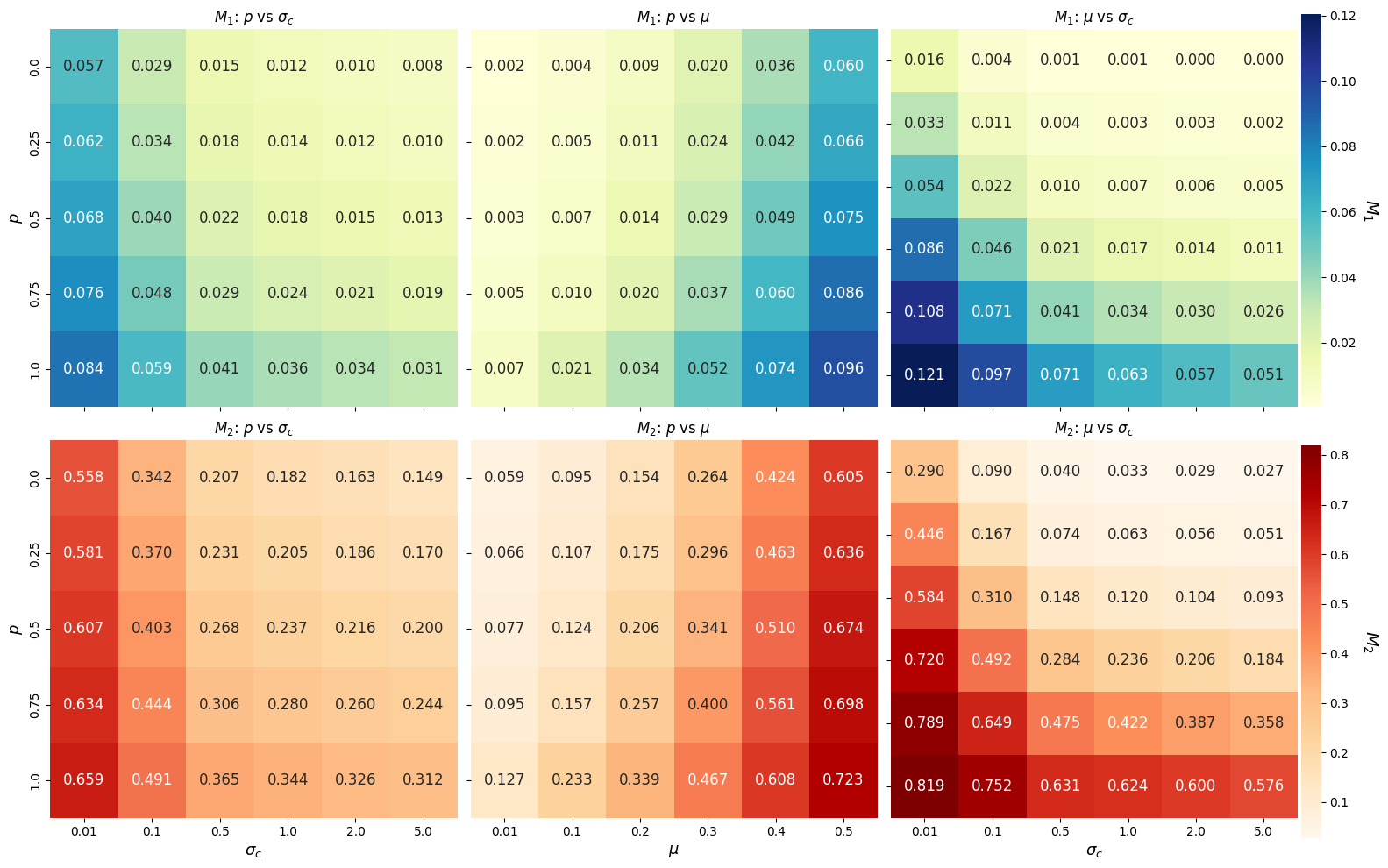
Evaluation using ElementCentricSimilarity metrics confirms FComDICE’s ability to modify network topology while maintaining crucial network characteristics. Quantitative results demonstrate an improvement of 20-30% in community concealment performance, as quantified by the M2 metric, when compared to baseline methods. This indicates that FComDICE effectively alters network structure to obscure community membership without significantly disrupting overall network integrity, as assessed by established network similarity measures.
Validating the Illusion: How Well Does It Actually Hide?
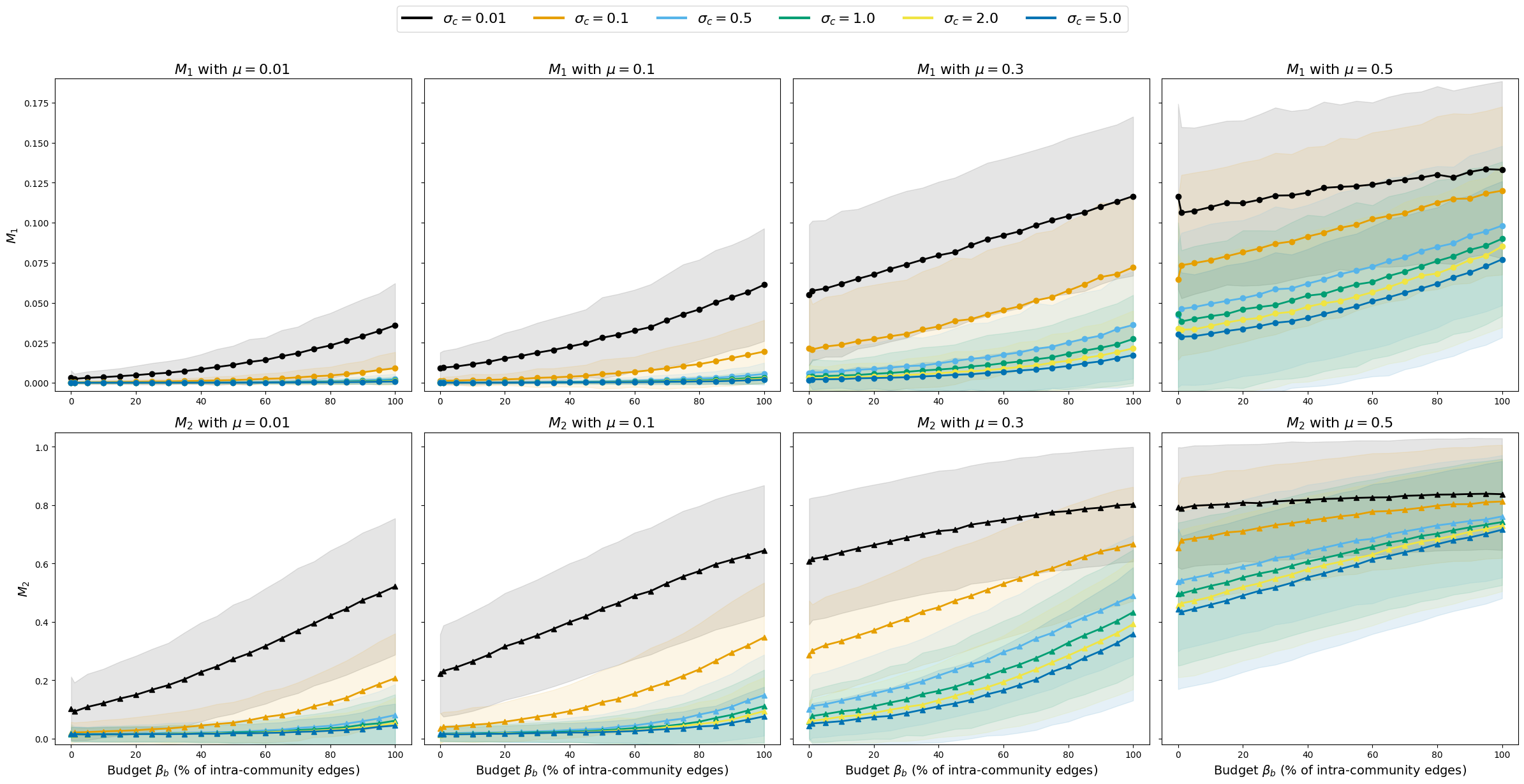
Researchers employ the LFRBenchmark to generate synthetic networks for evaluating community hiding algorithms due to its capacity for controlled experimentation. LFRBenchmark allows precise manipulation of network characteristics, including the number of communities, the mixing coefficient μ, and the average node degree, enabling systematic assessment of algorithm performance under defined conditions. This controlled environment is crucial for isolating the effectiveness of community hiding techniques and comparing results across different algorithms, as variations in network structure can significantly impact detection accuracy. The use of synthetic data ensures repeatability and facilitates rigorous statistical analysis of algorithm behavior.
Community detection was implemented using two distinct algorithms to establish a comparative baseline for evaluating hiding effectiveness: ‘GNNCommunityDetection’ and ‘ModularityMaximization’. ‘GNNCommunityDetection’ leverages graph neural networks to identify community structure, while ‘ModularityMaximization’ employs a greedy algorithm to optimize for the highest modularity score, a metric indicating the strength of division of a network into communities. The results obtained from these algorithms serve as a benchmark against which the performance of community hiding algorithms can be measured, allowing for quantitative assessment of their ability to obfuscate true community assignments.
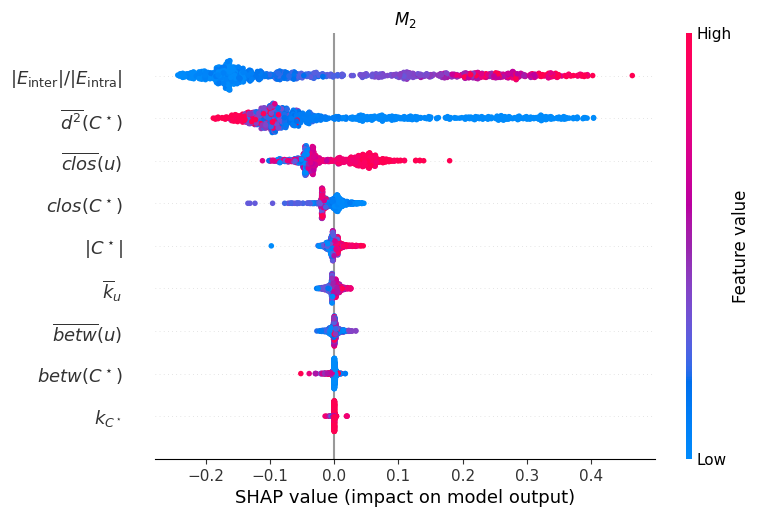
SHAPAnalysis was employed to identify the node features most impactful on community hidability. Results indicate that FComDICE demonstrates significant improvement over the baseline DICE algorithm under specific network conditions. Specifically, with a parameter setting of \mu = 0.01, FComDICE achieves M1 increases of up to 2000% compared to baseline DICE. This metric, M1, quantifies the degree to which a node’s community membership can be successfully hidden from detection, indicating a substantial enhancement in the algorithm’s ability to obscure community structure.
The Inevitable Arms Race: What Does This Mean for Security?
The capacity for effectively concealing network communities presents a notable threat to digital security paradigms. Malicious actors can leverage community hiding techniques to obscure critical infrastructure – such as power grids, financial networks, or communication systems – from detection, significantly increasing the potential for disruption or attack. Beyond infrastructure, sensitive data, including personally identifiable information or proprietary trade secrets, can be similarly shielded within hidden network structures, hindering security audits and incident response efforts. This ability to camouflage essential components creates blind spots for traditional monitoring systems, demanding a proactive shift towards more sophisticated detection methods capable of identifying anomalous behavior even within concealed network topologies. Consequently, understanding the mechanics of community hiding is no longer simply an academic exercise, but a vital component of robust cybersecurity strategies.
The capacity to detect and neutralize community hiding strategies is paramount for safeguarding network infrastructure against deliberate disruption. Adversarial attacks frequently exploit network topology to target critical nodes or propagate malicious content; concealing network communities effectively shields these vulnerabilities from standard detection methods. Consequently, research dedicated to mitigating these techniques – by developing algorithms that can identify artificially obscured communities or enhance network resilience to structural manipulation – is vital for maintaining operational integrity. Successfully countering community hiding doesn’t simply involve identifying disguised clusters, but also predicting how attackers might leverage these hidden structures, enabling proactive defenses and ensuring continued network functionality even under duress.
Continued advancement in network security necessitates the development of community hiding algorithms that are not only robust against evolving adversarial strategies but also adaptable to the dynamic nature of complex networks. Future investigations will likely center on refining these algorithms to maintain stable Element-Centric Similarity – a measure of how consistently network elements are grouped – even when subjected to substantial perturbations or modifications. Crucially, research should explore the synergistic relationship between feature engineering – the careful selection and transformation of network attributes – and overall network resilience, aiming to identify feature sets that enhance both the effectiveness of community hiding and the ability of the network to withstand attacks. This interdisciplinary approach promises to yield more secure and dependable network infrastructures capable of preserving critical information and functionality in increasingly hostile digital environments.
The pursuit of robust community detection, as explored in this paper, inevitably courts eventual exposure. FCom-DICE attempts to obfuscate communities through strategic graph perturbation and feature manipulation – a predictably temporary reprieve. It’s a familiar pattern; anything designed to be ‘self-healing’ or resistant to analysis simply hasn’t broken enough yet. As Linus Torvalds observed, “Most developers think lots of complex code equals being very clever. It doesn’t. It equals more bugs.” This holds true for adversarial defenses; each layer of complexity introduces new vulnerabilities, and the relentless pressure of production will inevitably reveal them. The paper’s focus on both structural and feature engineering is merely delaying the inevitable entropy, a testament to the cyclical nature of security and analysis.
What’s Next?
The pursuit of community concealment in graph data, as demonstrated by FCom-DICE, inevitably introduces a new class of detectable artifacts. Perturbing both structure and features offers marginal gains against increasingly sophisticated graph neural networks, but this is merely shifting the problem. Each layer of obfuscation is, in effect, a new signal for an adversary to learn. The inevitable outcome is an escalating arms race-a predictable consequence of attempting to outwit production systems.
Future work will likely focus on provable privacy guarantees, a quixotic endeavor given the inherent complexity of graph data. The real challenge isn’t hiding communities, but accepting that perfect concealment is impossible. Instead, research should explore controlled leakage-methods to introduce noise that preserves utility while frustrating precise community identification. This assumes, of course, that someone can define “utility” with sufficient precision-a dangerous assumption.
The current emphasis on adversarial attacks and counter-attacks is a distraction. The most significant threat remains the mundane: data breaches, sloppy implementation, and the eventual entropy of any complex system. CI is a temple, and the prayers for unbroken builds will continue, unanswered. Documentation, as always, remains a myth invented by managers.
Original article: https://arxiv.org/pdf/2602.12250.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Gold Rate Forecast
- Securing the Agent Ecosystem: Detecting Malicious Workflow Patterns
- Wuthering Waves – Galbrena build and materials guide
- 2025 Crypto Wallets: Secure, Smart, and Surprisingly Simple!
- The Best Directors of 2025
- Building 3D Worlds from Words: Is Reinforcement Learning the Key?
- Games That Faced Bans in Countries Over Political Themes
- The Most Anticipated Anime of 2026
- Most Famous Richards in the World
- Top 20 Educational Video Games
2026-02-15 10:36