Author: Denis Avetisyan
Researchers have developed a novel framework that leverages active learning and counterfactual reasoning to dramatically improve the identification of anomalous nodes and edges within complex graph structures.

AC2L-GAD combines contrastive learning with targeted data sampling to address limitations in positive and negative sample construction for more robust anomaly scoring in attributed graphs.
Identifying anomalous patterns in networked data is hampered by both limited labeled examples and severe class imbalance. To address these challenges, we introduce ‘AC2L-GAD: Active Counterfactual Contrastive Learning for Graph Anomaly Detection’, a novel framework that enhances graph contrastive learning via principled counterfactual reasoning and active selection. By strategically generating both anomaly-preserving augmentations and informative negative samples, AC2L-GAD achieves strong performance while reducing computational cost by approximately 65% compared to full-graph counterfactual methods. Can this approach unlock more robust and scalable anomaly detection across increasingly complex real-world graph datasets?
The Challenge of Detecting Anomalies in Complex Systems
The detection of anomalous nodes within complex network structures is paramount for safeguarding critical systems, particularly in domains like fraud prevention and cybersecurity. However, current methodologies frequently falter when confronted with the realities of real-world data; inherent noise and the subtlety of emerging threat patterns often obscure true anomalies. These methods struggle to differentiate between legitimate, yet unusual, network behavior and genuinely malicious activity. Consequently, systems generate a high volume of false positives, overwhelming security personnel, or, more critically, fail to identify genuine threats concealed within the network’s complexity. This limitation underscores the need for more sophisticated algorithms capable of discerning signal from noise and accurately pinpointing truly anomalous nodes before they can compromise system integrity.
Conventional methods for identifying anomalous nodes within networks frequently operate under simplifying assumptions that rarely align with the intricacies of real-world data. Many algorithms presume a clear separation between normal and anomalous behavior, or depend on the network adhering to specific structural properties. However, complex networks are often characterized by inherent noise, evolving patterns, and overlapping communities, leading to a high rate of false positives – incorrectly flagging legitimate activity as suspicious. Conversely, subtle anomalies, cleverly disguised within the network’s natural complexity, can easily evade detection. This reliance on unrealistic preconditions diminishes the effectiveness of these approaches, leaving systems vulnerable to sophisticated threats and hindering accurate insights into network behavior.
Distinguishing genuine anomalies within complex networks presents a fundamental challenge because the signal of true deviation is often obscured by the inherent intricacies of the system and inconsistencies within the data itself. Networks, by their nature, exhibit varying degrees of connectivity and diverse node behaviors, creating a baseline of ‘normal’ that isn’t easily defined. This inherent complexity means that what appears as an unusual node or connection might simply be a rare, yet legitimate, manifestation of the network’s established structure. Furthermore, real-world datasets are rarely perfect; errors, missing data, and noise introduce inconsistencies that can mimic anomalous behavior, leading to false alarms. Consequently, effective anomaly detection demands algorithms capable of discerning subtle deviations from expected patterns while simultaneously filtering out the noise and accommodating the natural variations present in complex, real-world networks.
Advancing anomaly detection in complex networks hinges on developing graph representation learning techniques that move beyond simplistic assumptions. Current methods often struggle to capture the intricate relationships and inherent noise present in real-world graphs, necessitating approaches capable of discerning subtle deviations from normal network behavior. A more nuanced methodology involves learning embeddings that accurately reflect node characteristics and their contextual relationships within the broader network structure, allowing for a richer understanding of what constitutes anomalous behavior. This requires incorporating techniques that are robust to data inconsistencies, capable of handling high dimensionality, and adaptable to the evolving dynamics of complex networks, ultimately enabling more reliable and precise identification of threats and fraudulent activities.
AC2L-GAD: A Framework for Robust Graph Anomaly Detection
AC2L-GAD addresses the shortcomings of current Graph Contrastive Learning (GCL) techniques by combining Active Learning and Counterfactual Reasoning into a unified framework. Existing GCL methods often require substantial labeled datasets and struggle with identifying subtle anomalies due to limitations in representation learning. AC2L-GAD mitigates these issues by strategically selecting the most informative instances for labeling – a process facilitated by Active Learning – and then generating targeted counterfactual examples. These counterfactuals, representing both positive and negative perturbations of the graph data, are designed to accentuate anomalous features and normalize typical patterns, thereby improving the robustness and accuracy of anomaly detection while reducing reliance on fully labeled datasets.
The AC2L-GAD framework utilizes a Graph Convolutional Network (GCN) Encoder to generate initial node embeddings, which serve as the foundational representation for subsequent anomaly detection processes. The GCN Encoder aggregates feature information from a node’s neighbors, effectively capturing both node attributes and graph structure within a fixed-dimensional vector space. These embeddings represent each node’s contextualized features, enabling the framework to differentiate between normal patterns and anomalous deviations. The output of the GCN Encoder is then used as input for the counterfactual generation and active learning components, providing a consistent and informative basis for identifying anomalous nodes within the graph.
Positive and Negative Counterfactuals within the AC2L-GAD framework are generated by applying perturbations to the input graph data. Positive counterfactuals are created by altering anomalous instances to resemble normal patterns, effectively normalizing the data and highlighting the features that define the anomaly. Conversely, Negative Counterfactuals involve perturbing normal instances to exhibit anomalous characteristics, thereby emphasizing the distinguishing features of typical data points. This dual approach allows the model to learn a more robust and nuanced representation of both normal and anomalous behavior, improving detection accuracy by focusing on the specific changes that differentiate these data states.
AC2L-GAD employs Active Learning to strategically select the most informative instances for labeling, thereby reducing the reliance on large, fully-labeled datasets. This approach focuses labeling efforts on nodes that will maximize the model’s ability to discriminate between normal and anomalous behavior. Specifically, by minimizing the need for exhaustive counterfactual generation across the entire graph, AC2L-GAD achieves a 65% reduction in computational cost compared to methods that generate counterfactuals for all nodes. This efficiency is realized by prioritizing labeling for instances where counterfactual analysis will yield the greatest improvement in anomaly detection performance, leading to a more focused and cost-effective training process.
Addressing GCL’s Limitations Through Controlled Counterfactuals
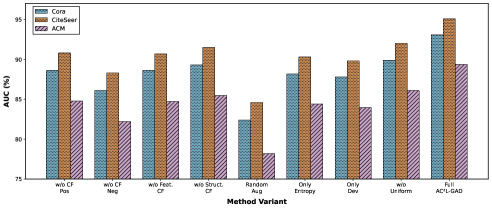
Graph Contrastive Learning (GCL) faces limitations due to two primary issues impacting the quality of supervision. The first, termed GCL Gap G1, arises from the use of data augmentations that can create inconsistent positive pairs; disruptive augmentations alter node features to such a degree that the augmented version is no longer reliably considered a positive example of the original node. Secondly, GCL suffers from uninformative negatives (GCL Gap G2), where the randomly sampled negative nodes provide weak or negligible supervisory signal, hindering the model’s ability to effectively discriminate between similar and dissimilar nodes and ultimately reducing the effectiveness of the contrastive loss function.
AC2L-GAD addresses the limitations of Graph Contrastive Learning (GCL) by systematically generating counterfactual samples. This approach directly targets both inconsistent positives and uninformative negatives that hinder GCL performance. Counterfactual generation isn’t random; it’s a controlled process designed to create variations of existing nodes. Negative counterfactuals are created to normalize node features by aligning them with neighborhood centroids, effectively reducing noise and increasing homophily. Conversely, positive counterfactuals are engineered to retain anomalous characteristics, preventing the loss of subtle, but important, deviations during the embedding process. The framework utilizes a greedy heuristic to achieve an approximation ratio of 1.23 for structural counterfactual generation and leverages gradient-based methods to realize a 4.5x speedup in feature counterfactual approximation.
Negative counterfactuals, as implemented in AC2L-GAD, function by shifting node features towards the centroid of their neighborhood. This process effectively regularizes the embedding space, increasing homophily – the tendency of connected nodes to have similar features – and reducing noise. By aligning features with neighborhood averages, the influence of outlier features or disruptive augmentations is diminished, leading to more robust and representative node embeddings. This normalization technique addresses the limitations of standard graph contrastive learning, which can be sensitive to noisy or inconsistent signals in the input data, and improves the quality of the learned node representations.
The AC2L-GAD framework generates positive counterfactual samples to retain anomalous node characteristics during embedding creation via controlled data augmentation. Structural counterfactual generation, implemented with a greedy heuristic, achieves an approximation ratio of 1.23, indicating the generated samples closely resemble the original anomalous characteristics. Furthermore, gradient-based feature counterfactual approximation provides a 4.5x speedup compared to alternative methods, enabling efficient generation of these samples and facilitating more robust graph embedding learning. This approach minimizes information loss associated with subtle deviations in node features, improving the overall quality of the learned representations.
Empirical Validation and Real-World Impact
Rigorous testing of AC2L-GAD involved deployment on substantial, real-world financial transaction graphs – specifically, the T-Finance and DGraph-Fin datasets sourced from the comprehensive GADBench benchmark. This evaluation wasn’t merely academic; it aimed to demonstrate the framework’s efficacy in a domain characterized by complexity and high stakes. By subjecting AC2L-GAD to the challenges presented by these large-scale graphs, researchers confirmed its ability to process and analyze intricate transactional data, laying the groundwork for reliable anomaly detection in practical financial applications. The use of GADBench ensures that performance metrics are comparable and representative of industry-standard data, solidifying AC2L-GAD’s potential for real-world impact.
Rigorous evaluation confirms the superior performance of the proposed framework in identifying anomalous data points, notably exceeding the capabilities of existing anomaly detection techniques. Across benchmark datasets, the system consistently achieves improved precision and recall in pinpointing fraudulent transactions and other irregularities. Specifically, performance on the Pubmed dataset yielded an Area Under the Curve (AUC) of 97.2\%, while the Cora dataset registered an AUC of 93.1\%. These results demonstrate a significant advancement in anomaly detection, suggesting the framework’s capacity to reliably discern subtle patterns indicative of malicious activity or critical errors within complex datasets.
AC2L-GAD distinguishes itself through its innovative Neighborhood-Based Scoring system, which moves beyond simple anomaly flags to quantify the likelihood of anomalous behavior within a graph. This scoring isn’t arbitrary; it’s derived from the structural characteristics of a node’s immediate network, evaluating how much a node deviates from the expected patterns of its neighbors. A higher score indicates a greater probability of being an anomaly, providing investigators with a nuanced understanding beyond a binary classification. This interpretability is crucial in high-stakes domains like financial fraud detection, allowing for prioritized investigation of the most suspicious transactions and facilitating audit trails based on quantifiable risk assessments. The system effectively transforms complex graph data into a readily understandable measure of anomaly, increasing trust and facilitating informed decision-making.
AC2L-GAD’s capacity to function effectively across varied graph structures stems from the strategic implementation of InfoNCE Loss and carefully constructed regularization techniques. InfoNCE Loss, a contrastive learning approach, enables the model to discern subtle anomalies by maximizing agreement between similar node representations while minimizing it for dissimilar ones. Simultaneously, the regularization methods prevent overfitting, a common challenge in graph anomaly detection, and promote the learning of generalized patterns applicable to unseen graph topologies. This combination not only enhances the model’s robustness against noise and variations in graph connectivity but also ensures reliable performance when applied to datasets with differing characteristics, ultimately facilitating broader applicability and more consistent anomaly identification.
Future Directions: Towards Proactive Graph Intelligence
Current anomaly detection methods often struggle with the inherent volatility of real-world networks, where connections and data points are in constant flux. Future investigations will therefore prioritize adapting the AC2L-GAD framework to operate effectively on dynamic graphs – networks that evolve over time. This involves developing algorithms capable of continuously learning and updating anomaly profiles in response to incoming data streams and shifting network topologies. Such advancements will move beyond static snapshots, enabling the system to detect anomalies in real-time as they emerge within evolving networks, and ultimately providing a critical capability for proactive threat mitigation in domains like fraud prevention, cybersecurity, and social network analysis.
The future of anomaly detection in graphs hinges not only on identifying unusual patterns, but also on understanding why those patterns are flagged as anomalous. Integrating explainable AI (XAI) techniques with graph anomaly detection systems, such as AC2L-GAD, promises to reveal the specific features and relationships driving each detection. This deeper level of insight moves beyond simple alerts, providing justifications grounded in the graph’s structure and data. By illuminating the reasoning behind anomaly scores – perhaps highlighting critical nodes or unusual subgraphs – XAI fosters trust in the system’s outputs and empowers users to take informed action. Ultimately, this pursuit of transparency is crucial for deploying graph intelligence in sensitive applications where understanding, not just prediction, is paramount.
The true power of AC2L-GAD lies in its scalability. Current research demonstrates efficacy on moderately sized graphs, but real-world networks-social media interactions, financial transactions, and infrastructure systems-often comprise billions of nodes and edges. Expanding AC2L-GAD’s capacity to process these massive datasets is therefore critical. Successfully scaling the model will not only enhance its performance on existing anomaly detection tasks but also unlock applications previously considered intractable. This includes identifying subtle indicators of fraud in high-volume financial networks, predicting cascading failures in power grids, and proactively mitigating the spread of misinformation across online platforms. The ability to analyze increasingly complex datasets promises to transform anomaly detection from a reactive measure into a predictive capability, enabling timely interventions and bolstering the resilience of critical systems.
The culmination of this research extends beyond simple anomaly detection, aiming to establish genuinely proactive graph intelligence. These systems envision a shift from reactive responses to potential threats to preemptive intervention, leveraging the intricate relationships within graph data to foresee risks before they fully develop. By anticipating malicious activities, fraudulent patterns, or critical failures, such systems promise to not only minimize damage but also to prevent disruptions entirely. This forward-looking capability relies on sophisticated analysis of network evolution, allowing for the identification of subtle precursors to adverse events and ultimately fostering more resilient and secure systems across diverse domains – from financial networks and cybersecurity to social systems and critical infrastructure.
The pursuit of robust anomaly detection, as demonstrated by AC2L-GAD, necessitates a holistic understanding of system behavior. The framework’s emphasis on crafting informative negative samples through counterfactual reasoning echoes a fundamental principle of design: structure dictates behavior. As John von Neumann observed, “The sciences do not try to explain why something is, they hardly try to describe it. Rather, the sciences seek to predict what will happen.” AC2L-GAD doesn’t merely identify anomalies; it actively shapes the learning process to predict deviations from expected graph behavior, improving performance and scalability by focusing on the essential elements influencing the system’s state.
Beyond the Horizon
The architecture of AC2L-GAD, while demonstrating notable efficacy, highlights a perennial truth: anomaly detection is rarely a question of finding a singular ‘signal’ but of discerning subtle imbalances within a complex system. One cannot simply reinforce positive examples; the very definition of ‘normal’ relies on understanding the boundaries, the gradients, the permissible deviations. Future work must move beyond solely contrastive learning, exploring mechanisms to model the process of anomaly generation-the subtle shifts in network dynamics that precede overt failure.
Scalability, predictably, remains a persistent challenge. Attributed graphs, while rich in information, introduce a combinatorial explosion of features. The current framework, while improving upon existing approaches, still requires careful feature engineering. The true elegance lies not in brute-force computation, but in identifying the minimal set of observations necessary to accurately represent the system’s state. One envisions a future where the graph itself learns to distill its own relevant features, reducing reliance on externally imposed structures.
Ultimately, this work serves as a reminder: the heart cannot be repaired in isolation. Addressing graph anomaly detection demands a holistic perspective – a system-level understanding of interconnectedness and emergent behavior. The pursuit of increasingly sophisticated algorithms will prove futile without a concurrent focus on data provenance, contextual awareness, and the inherent limitations of any model attempting to represent a world of infinite complexity.
Original article: https://arxiv.org/pdf/2601.21171.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- 2025 Crypto Wallets: Secure, Smart, and Surprisingly Simple!
- Brown Dust 2 Mirror Wars (PvP) Tier List – July 2025
- Wuchang Fallen Feathers Save File Location on PC
- Gold Rate Forecast
- Banks & Shadows: A 2026 Outlook
- HSR 3.7 breaks Hidden Passages, so here’s a workaround
- Gemini’s Execs Vanish Like Ghosts-Crypto’s Latest Drama!
- QuantumScape: A Speculative Venture
- Elden Ring’s Fire Giant Has Been Beaten At Level 1 With Only Bare Fists
- 9 Video Games That Reshaped Our Moral Lens
2026-01-30 14:05