Author: Denis Avetisyan
Researchers have developed a novel framework that tackles the challenges of identifying anomalies in dynamic, imbalanced graph data.

This paper introduces BAED, a balanced anomaly-guided ego-graph diffusion model for effective inductive graph anomaly detection, achieving state-of-the-art performance through diffusion models and curriculum learning.
Despite advancements in graph neural networks, effectively detecting anomalies in dynamic, real-world networks remains challenging due to both the scarcity of anomalous data and the limitations of static graph assumptions. This paper introduces ‘Balanced Anomaly-guided Ego-graph Diffusion Model for Inductive Graph Anomaly Detection’, a novel framework-BAED-that addresses these issues by synthesizing balanced, anomaly-aligned ego-graphs via a diffusion model and employing a curriculum learning strategy. Experimental results demonstrate that BAED improves anomaly detection and generalization across five datasets, overcoming limitations of existing transductive methods. Could this data-centric approach unlock more robust and scalable solutions for graph anomaly detection in evolving network environments?
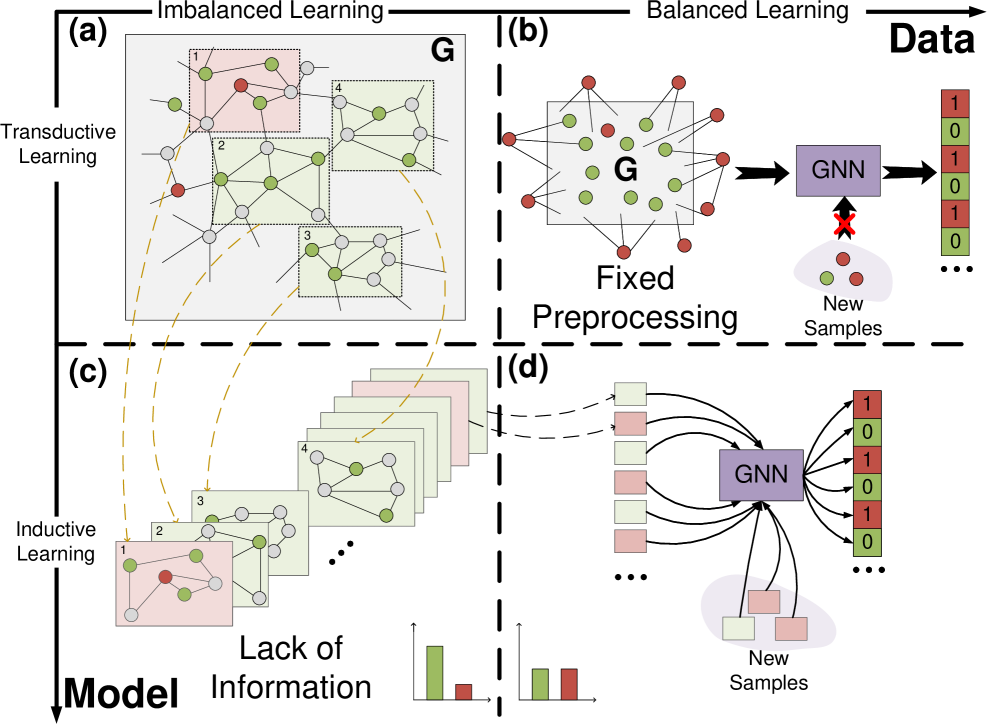
Deconstructing the Network: The Challenge of Anomaly Detection
As data increasingly manifests as interconnected networks – social networks, financial transactions, biological pathways – traditional anomaly detection techniques face mounting difficulties. These methods, often designed for independent data points, struggle to discern meaningful deviations within the intricate web of relationships defining graph-structured data. The sheer scale of modern graphs, boasting millions or even billions of nodes and edges, exacerbates this problem, creating a computational bottleneck. More critically, subtle anomalies – a fraudulent transaction masked by legitimate activity, a malfunctioning sensor appearing normal within a network – can evade detection because these techniques fail to adequately consider the contextual information embedded within the graph’s structure. Consequently, critical deviations, potentially signaling fraud, security breaches, or systemic failures, remain hidden, underscoring the need for specialized approaches capable of navigating and interpreting complex relational data.
Effective anomaly detection within complex graphs demands a nuanced approach that transcends simple node-level analysis. Identifying unusual nodes isn’t solely about their individual properties; it’s fundamentally about understanding their position and connections within the larger network. A node might appear normal in isolation, yet exhibit anomalous behavior when considered alongside its neighbors and the broader relational structure of the graph. Consequently, algorithms must integrate both the intrinsic characteristics of each node and the contextual information derived from its surrounding network topology. This requires methods capable of simultaneously assessing local node features – such as degree, centrality, or attribute values – and global patterns of connectivity to discern deviations that would otherwise remain hidden, offering a more holistic and accurate assessment of anomalous behavior.
The reliable identification of anomalous nodes within complex graph structures is frequently hampered by a significant class imbalance. This disparity, where instances representing deviations or outliers are drastically outnumbered by normal nodes, presents a substantial challenge to machine learning algorithms. Most models are designed with the assumption of relatively balanced classes, and thus exhibit a pronounced bias towards the majority class – often leading to a high false negative rate for anomalies. Consequently, even subtle but critical deviations can be overlooked, as the model prioritizes accurately classifying the abundant normal nodes. Addressing this imbalance requires specialized techniques, such as weighted loss functions, resampling strategies, or anomaly-specific algorithms, to ensure that the model can effectively learn and detect these rare, yet potentially significant, instances within the graph.
Forging New Paths: BAED – A Framework for Inductive Graph Anomaly Detection
The BAED framework addresses inductive graph anomaly detection by integrating diffusion models with curriculum anomaly augmentation. This approach leverages the generative capabilities of diffusion models to create synthetic anomalous subgraphs, thereby expanding the training dataset beyond observed anomalies. Curriculum learning is then applied, strategically increasing the difficulty of generated anomalies during training to improve model robustness and generalization. This combination allows BAED to detect anomalies in previously unseen graphs – a core requirement of inductive anomaly detection – by learning a robust representation of both normal and anomalous graph structures. The framework differs from traditional methods by not requiring retraining when encountering new graph structures.
BAED employs an Ego-Graph Diffusion Model as its primary data augmentation technique. This model operates by generating anomalous subgraphs, termed “ego-graphs,” centered around individual nodes within the larger graph structure. The diffusion process involves iteratively adding and modifying edges and node features to create realistic anomalous patterns. By generating these synthetic anomalous ego-graphs, BAED effectively expands the training dataset with diverse examples of graph anomalies. This data augmentation strategy addresses the scarcity of labeled anomalous data, which is common in real-world graph anomaly detection scenarios, and significantly improves the model’s ability to generalize to unseen anomalous instances. The generated anomalies are designed to mimic plausible deviations from normal graph behavior, enhancing the robustness of the anomaly detection process.
Anomaly-Guidance Embedding within the BAED framework functions by learning a latent representation of anomalous patterns directly from the graph structure. This embedding is then used to guide the diffusion process, ensuring generated anomalies align with the inherent characteristics of the graph. Specifically, the embedding conditions the diffusion model to prioritize the creation of anomalies that are structurally plausible and contextually relevant, preventing the generation of unrealistic or irrelevant perturbations. This approach differs from random anomaly injection by focusing on anomalies that reflect meaningful deviations within the graph’s established relationships and node features, thereby enhancing the model’s ability to detect subtle, yet significant, anomalous behaviors.
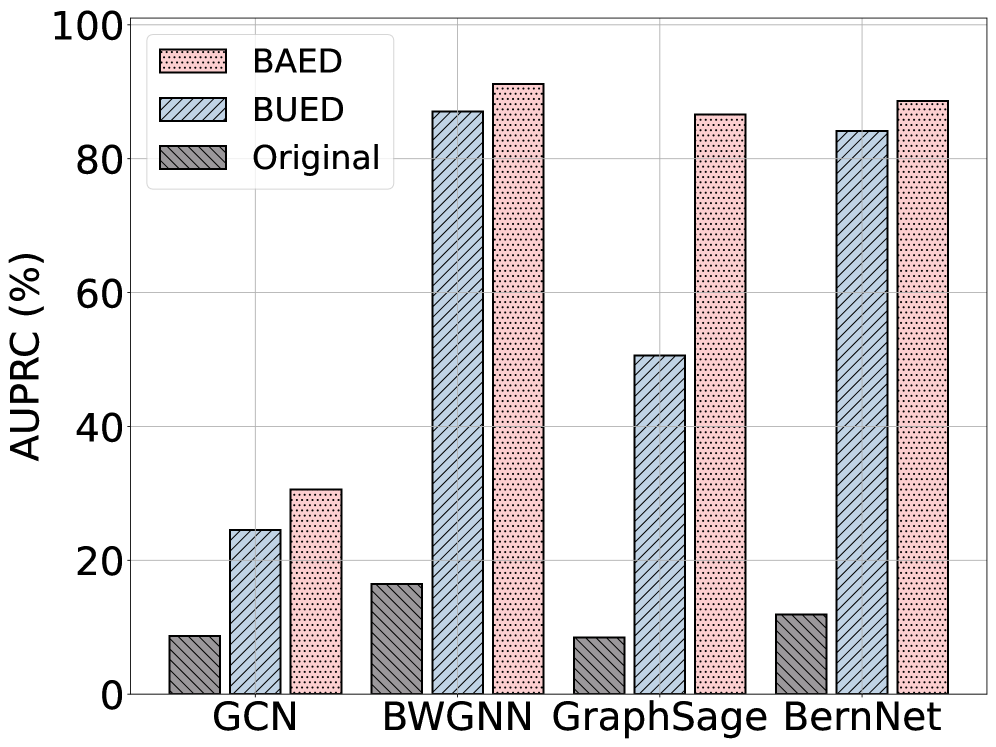
The BAED framework mitigates the common problem of class imbalance in graph anomaly detection by employing strategic anomalous sample generation during the training process. This approach directly addresses the typically limited availability of anomalous data, improving model performance on imbalanced datasets. Evaluations on the T-Finance dataset demonstrate significant improvements in anomaly detection capability, achieving up to a 90.93% increase in Area Under the Receiver Operating Characteristic curve (AUROC) and an 84.84% increase in Area Under the Precision-Recall Curve (AUPRC) when compared to existing anomaly detection methods.
Dissecting the Mechanism: How BAED Generates Realistic Anomalies
The Ego-Graph Diffusion Model enhances standard Diffusion Models by shifting the operational focus from the entire graph to individual node-centric ego-graphs. An ego-graph represents the local neighborhood of a given node, comprising the node itself and all directly connected edges and nodes. By applying the diffusion process-a technique of progressively adding noise and then learning to reverse the process-to these ego-graphs, the model learns to generate realistic perturbations within the immediate context of each node. This localized approach allows for more nuanced anomaly generation, as the model considers the specific relationships and features of each node’s direct neighbors, rather than treating the graph as a monolithic entity. The resultant anomalies are thus constrained by the local graph structure, increasing their plausibility and contextual relevance.
BAED generates contextually relevant anomalies by leveraging the ego-graph structure of the input data. Instead of treating each node in isolation, the model considers the immediate neighborhood – the ego-graph – of each node during anomaly generation. This ensures that any generated anomalous features are consistent with the existing relationships and attributes of connected nodes. Consequently, the anomalies are not random perturbations but rather plausible deviations within the established network context, reflecting the complex interdependencies inherent in graph-structured data. This approach allows for the creation of more realistic and challenging anomalies compared to methods that ignore local graph connectivity.
Curriculum Anomaly Augmentation (CAA) operates by progressively increasing the difficulty of anomalous samples generated during training. Initially, the model is exposed to simpler anomalies that are easily detectable, facilitating rapid initial learning. As the model’s performance, as measured by its ability to correctly identify anomalies, improves, CAA dynamically shifts the generation process to focus on more complex and subtle anomalies. This adjustment is typically achieved by modifying parameters controlling the severity or characteristics of the injected anomalies, or by altering the sampling strategy to prioritize harder-to-detect examples. The objective is to maintain an optimal learning rate by consistently presenting challenging, yet attainable, anomalous data, thereby enhancing the model’s robustness and generalization capability.
The foundation of BAED’s anomaly generation process is a Graph Neural Network (GNN) responsible for learning a robust encoding of the input graph’s structural information. This GNN operates by iteratively aggregating and transforming feature information from each node’s neighborhood, effectively capturing both local and global relationships within the graph. The resulting node embeddings, which represent the learned graph structure, are then used as input to the Ego-Graph Diffusion Model for anomaly generation. The performance of the GNN, specifically its ability to accurately represent node relationships and graph topology, directly impacts the quality and realism of the generated anomalies; a poorly trained GNN will produce embeddings that fail to capture critical structural features, leading to anomalies that are either implausible or lack contextual relevance.
Beyond the Algorithm: Implications and Future Trajectories
The escalating complexity of real-world networks demands robust anomaly detection methods, and the BAED framework offers a promising solution specifically tailored for dynamic graphs – those where connections and nodes are constantly evolving. Unlike traditional approaches, BAED excels in identifying unusual patterns within these shifting structures, a capability crucial for applications like fraud detection, where malicious transactions rapidly adapt, and network security, where attacks manifest as fleeting, anomalous connections. This ability to perform reliably in non-stationary environments stems from BAED’s innovative approach to anomaly generation, allowing it to accurately model evolving network behavior and flag deviations that would otherwise go unnoticed. Consequently, the framework represents a significant step toward proactive threat identification and improved resilience in increasingly interconnected systems.
A key strength of the proposed framework lies in its inductive capacity, enabling effective generalization to previously unseen graphs and nodes. This characteristic significantly diminishes the necessity for exhaustive retraining when confronted with novel network structures or the addition of new entities. Unlike methods heavily reliant on memorization of training data, the framework learns underlying patterns and relationships within the graph, allowing it to accurately identify anomalies even in contexts it has not explicitly encountered. This adaptability is particularly valuable in dynamic real-world systems, where graphs are constantly evolving, and the computational cost of frequent retraining can be prohibitive, offering a practical and scalable solution for ongoing anomaly detection.
A key strength of the BAED framework lies in its computational efficiency. Evaluations demonstrate a substantial 27.98% reduction in runtime when compared to the CGenGA method, representing a significant advancement for real-time anomaly detection applications. This improved speed allows for more frequent and comprehensive graph analysis, particularly crucial in dynamic systems where rapid identification of unusual activity is paramount. The reduction in processing time not only lowers operational costs but also enables BAED to scale effectively to larger and more complex network datasets, facilitating broader implementation across various security and monitoring domains.
Building upon its current performance, which includes a 4.97% Area Under the Receiver Operating Characteristic (AUROC) improvement on the Elliptic dataset when contrasted with the Baseline Walk Generation Neural Network (BWGNN), future research aims to refine the BAED framework by incorporating complementary anomaly generation strategies. Specifically, integrating techniques like CGenGA alongside BAED’s existing methods promises to expand the diversity and realism of synthetic anomalies. This combined approach could provide a more robust training dataset, allowing anomaly detectors to generalize more effectively to subtle and previously unseen malicious patterns within dynamic graph structures, ultimately enhancing the accuracy and reliability of fraud detection and network security systems.
The pursuit of identifying anomalous nodes within a graph inherently demands a disruption of established patterns. This research, with its Balanced Anomaly-guided Ego-graph Diffusion Model (BAED), embodies that principle. It doesn’t simply accept the graph’s structure as immutable; instead, it actively diffuses and augments the data, effectively breaking and rebuilding the network to expose vulnerabilities. As Claude Shannon famously stated, “The most important thing is to keep the channel open.” BAED applies this by continually refining the ‘channel’ of information flow within the graph, enhancing the signal of anomalies even amidst imbalanced datasets and dynamic structural shifts. The diffusion process itself is a calculated perturbation, a controlled dismantling that reveals the underlying weaknesses-much like reverse-engineering a system to understand its limits.
Beyond the Horizon
The pursuit of anomaly detection, particularly within the complex architecture of dynamic graphs, rarely yields definitive closure. This work, while demonstrating a compelling approach to imbalanced learning and inductive generalization, implicitly acknowledges the inherent instability of ‘normality’ itself. The very act of defining a diffusion process relies on assumptions about underlying data distributions – assumptions destined to be violated by the evolving nature of real-world graphs. Future investigations shouldn’t merely refine the augmentation strategies or network architectures, but directly confront the epistemological question: at what point does the ‘anomaly’ become the new normal?
A logical, if unsettling, extension of this line of inquiry involves deliberately introducing controlled ‘perturbations’ into the graph structure during training. Rather than treating anomalies as deviations to be identified, one might consider them as exploratory probes, designed to stress-test the system’s understanding of connectivity and function. The goal isn’t flawless prediction, but robust adaptation – a system capable of incorporating unexpected changes without catastrophic failure.
Ultimately, the true challenge lies not in detecting what is abnormal, but in anticipating what could become abnormal. A model that passively observes a static graph is, by definition, limited. The next iteration demands a system that actively interrogates its environment, seeking out potential vulnerabilities and proactively adjusting its internal representation of ‘normal’ behavior. This necessitates a shift from predictive accuracy to adaptive resilience.
Original article: https://arxiv.org/pdf/2602.05232.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- 21 Movies Filmed in Real Abandoned Locations
- 2025 Crypto Wallets: Secure, Smart, and Surprisingly Simple!
- The 11 Elden Ring: Nightreign DLC features that would surprise and delight the biggest FromSoftware fans
- 10 Hulu Originals You’re Missing Out On
- 39th Developer Notes: 2.5th Anniversary Update
- Gold Rate Forecast
- Bitcoin, USDT, and Others: Which Cryptocurrencies Work Best for Online Casinos According to ArabTopCasino
- Tainted Grail: The Fall of Avalon Expansion Sanctuary of Sarras Revealed for Next Week
- PLURIBUS’ Best Moments Are Also Its Smallest
- Noble’s Slide and a Fund’s Quiet Recalibration
2026-02-06 12:51