Author: Denis Avetisyan
Researchers have developed a novel generative model to create network traffic that more accurately reflects real-world patterns, improving the effectiveness of security testing and training.
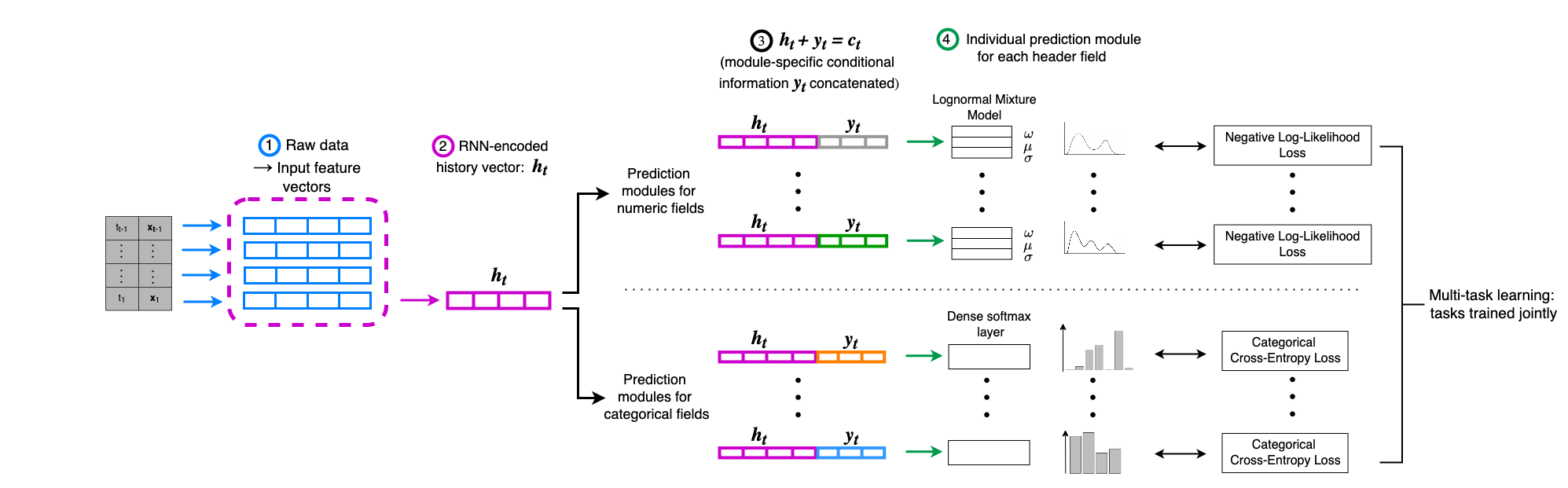
TempoNet leverages Temporal Point Processes and multi-task learning to generate synthetic network traffic for applications like anomaly detection and cyber range environments.
Generating realistic network traffic is crucial for robust security evaluation, yet accurately modeling the complex temporal dynamics of real-world networks remains a significant challenge. This paper introduces TempoNet: Learning Realistic Communication and Timing Patterns for Network Traffic Simulation, a novel generative model that leverages multi-task learning and temporal point processes to jointly model both inter-arrival times and packet/flow characteristics. TempoNet captures fine-grained timing and higher-order correlations, surpassing limitations of existing GAN-, LLM-, and Bayesian-based approaches, and producing high-fidelity traces validated against real-world data. Will this improved realism in synthetic traffic generation ultimately lead to more effective and proactive cybersecurity defenses?
Deconstructing Reality: The Illusion of Network Fidelity
Conventional network simulations frequently employ abstractions that sacrifice the nuanced temporal characteristics of live traffic, potentially yielding inaccurate results. These simplified models often treat packets as arriving randomly, ignoring critical patterns like bursts, correlations between flows, and the impact of queuing delays-all commonplace in real-world networks. Consequently, security systems tested against such synthetic traffic may exhibit vulnerabilities when confronted with authentic attacks, and performance evaluations could underestimate congestion or overestimate capacity. This discrepancy arises because real network traffic isn’t uniformly distributed; instead, it displays self-similarity and long-range dependence, meaning patterns at one timescale are reflected at others. Capturing these intricate temporal dynamics is paramount for simulations aiming to faithfully represent network behavior and provide reliable insights into system resilience and efficiency.
Accurate security assessments, the refinement of intrusion detection systems, and comprehensive network performance analysis all fundamentally depend on the realism of the traffic used for testing. Simplified or artificial traffic patterns can yield misleading results, failing to expose vulnerabilities or accurately predict how a network will behave under genuine conditions. Consequently, the ability to generate network traffic that faithfully replicates the characteristics of real-world usage – including variations in packet size, inter-arrival times, and application protocols – is paramount. This demands not only statistical similarity but also the capture of complex temporal dependencies and anomalies that differentiate benign activity from malicious attacks, ensuring that security tools and network designs are truly robust and resilient.
Relying on packet capture (PCAP) replay for network testing presents significant limitations. While seemingly straightforward, this technique inherently lacks the diversity of real-world traffic patterns; PCAP files represent a specific moment in time and cannot account for evolving threats or user behaviors. Consequently, security systems tested solely with replayed traffic may exhibit vulnerabilities when confronted with novel attacks. Furthermore, PCAP files often contain sensitive data, including usernames, passwords, and confidential communications, raising substantial privacy and compliance concerns if exposed during testing or shared between parties. The static nature of replay, coupled with potential data breaches, necessitates the development of more dynamic and privacy-preserving methods for generating realistic network traffic.
The increasing need for network simulations that accurately reflect real-world conditions has spurred significant investigation into generative models as a means of creating synthetic traffic. These models, leveraging techniques like Generative Adversarial Networks (GANs) and Variational Autoencoders, aim to produce traffic patterns statistically indistinguishable from live network data, offering scalability beyond simple packet capture replay. However, substantial challenges persist; maintaining high fidelity – ensuring the synthetic traffic accurately mimics the nuanced characteristics of real traffic – is computationally intensive and requires extensive training datasets. Equally important is compliance – the generated traffic must adhere to network protocols and avoid inadvertently creating malicious or invalid packets. Successfully navigating these hurdles is critical for realizing the full potential of generative models in security testing, performance analysis, and the development of robust network infrastructure.
TempoNet: Weaving Temporal Patterns into Network Reality
TempoNet is a generative model designed to synthesize realistic network traffic data by integrating Temporal Point Processes (TPPs) with a multi-task learning framework. TPPs are employed to model the timing of discrete network events, allowing the model to learn and reproduce the complex temporal dependencies observed in real-world network activity. The multi-task learning component enables TempoNet to simultaneously capture various facets of network behavior, improving generalization performance and the overall fidelity of the generated traffic. This approach differs from traditional methods by explicitly modeling the time dimension of network events, resulting in more authentic and nuanced synthetic datasets for network analysis and testing.
TempoNet employs Temporal Point Processes (TPPs) to model network traffic by representing events as points in time. Unlike traditional methods that assume fixed or independent event rates, TPPs explicitly model the temporal dependencies between events, capturing the probability of an event occurring given the history of prior events. This is achieved by defining an intensity function, \lambda(t | history), which represents the instantaneous rate of event occurrence at time t conditional on the past event sequence. By learning these intensity functions from real network traces, TempoNet accurately reproduces the complex inter-arrival time distributions observed in live traffic, including phenomena like bursts, self-similarity, and long-range dependence. The model’s ability to capture these temporal patterns is crucial for generating realistic network simulations and evaluating network performance under varying conditions.
Multi-task learning within TempoNet improves generalization and realism by simultaneously optimizing for the generation of multiple network characteristics. Instead of training separate models for each attribute – such as packet size, inter-arrival time, and flow duration – a single model learns to predict all of these features concurrently. This shared learning process allows the model to identify correlations between different network behaviors, leading to more consistent and realistic traffic generation. Specifically, the model utilizes shared representations across tasks, enabling knowledge transfer and reducing the risk of overfitting to individual features. This approach results in a more robust and accurate representation of real-world network dynamics compared to single-task learning methods.
TempoNet employs a Log-Normal Mixture Model to represent the distribution of inter-arrival times within network traffic, directly addressing the need for high temporal fidelity. This model assumes that inter-arrival times are generated from a mixture of log-normal distributions, allowing it to capture the multi-modal nature often observed in real network data. Specifically, the model estimates parameters – means and standard deviations – for each component of the mixture, alongside mixing coefficients determining the weight of each component. By accurately modeling the distribution of these intervals, TempoNet avoids the limitations of simpler models, such as Poisson processes, which assume exponentially distributed inter-arrival times and fail to capture the burstiness and self-similarity common in network traffic. This approach allows for more realistic generation of network event sequences, improving the overall fidelity of simulated network behavior.

Validating the Illusion: Realism, Compliance, and Coverage
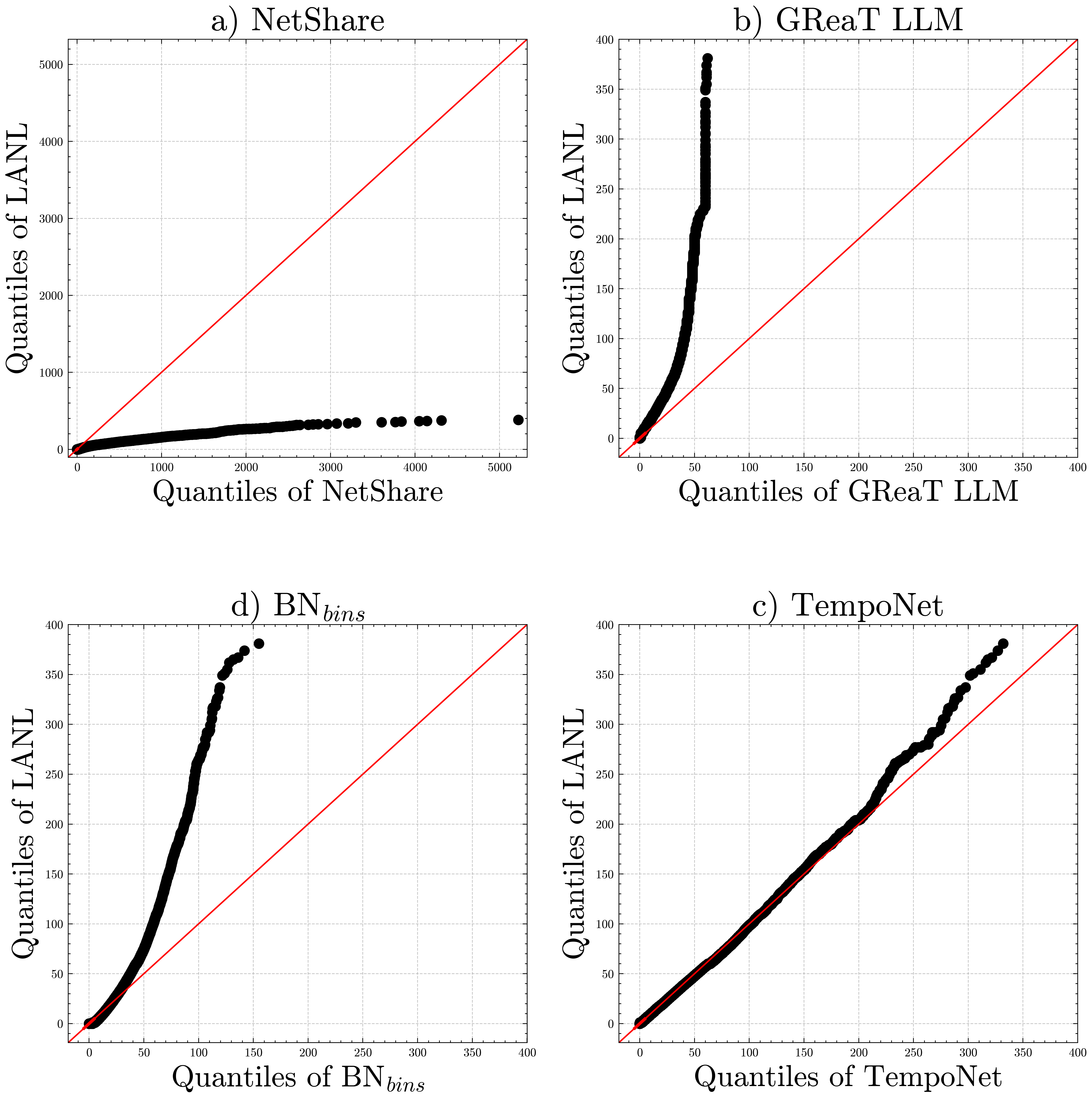
TempoNet consistently generates network traffic with a higher degree of realism compared to existing methods, as quantified by Earth Mover’s Distance (EMD) scores. Evaluations across the LANL, CIDDS, and DC datasets demonstrate TempoNet achieving the lowest EMD scores for both inter-arrival times and flow durations. The EMD metric assesses the statistical distance between the generated traffic’s distributions and those observed in real-world network captures; lower scores indicate a closer match. These results confirm TempoNet’s ability to accurately replicate the timing characteristics of network traffic, a critical factor for realistic network simulation and security testing.
TempoNet’s traffic generation process incorporates validation against established network protocol specifications, specifically ensuring all generated packets conform to defined structures and permissible values for each field. This adherence to protocol rules prevents the creation of malformed or invalid packets that would be rejected by network devices or cause parsing errors. The system verifies header fields, payload lengths, and flag combinations against relevant standards-including TCP, UDP, and IP-before outputting the traffic. This compliance is a critical feature for realistic network simulations and security testing, as it avoids introducing artifacts stemming from syntactically incorrect packets and allows for accurate evaluation of network component behavior.
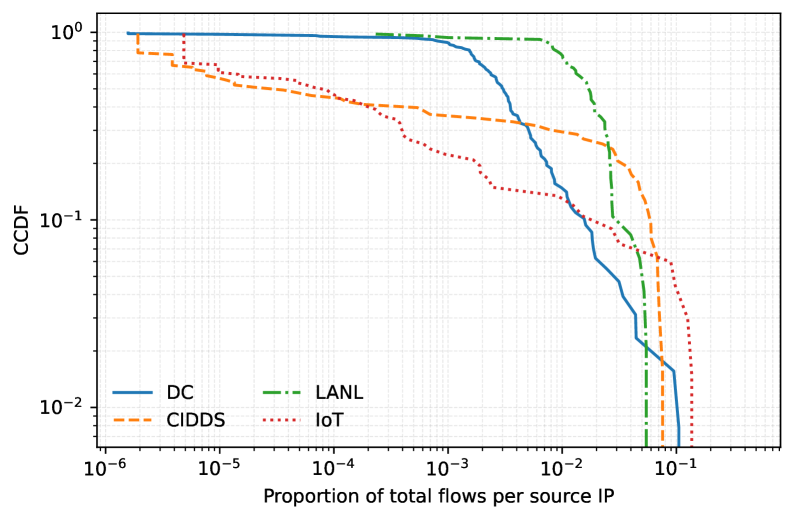
TempoNet utilizes a multi-task learning approach to improve the diversity of generated network traffic. Evaluation across the LANL, CIDDS, and DC datasets demonstrates TempoNet achieves the highest coverage scores when compared to existing traffic generation methods. Coverage, in this context, quantifies the proportion of unique traffic patterns represented in the generated data, directly indicating a broader range of network behaviors. This enhanced diversity is critical for comprehensive security testing, as it allows for exposure to a wider spectrum of potential attack vectors and anomalous behaviors that might be missed by systems tested with less varied traffic.
Evaluation using the CIDDS dataset demonstrates TempoNet’s ability to generate structurally accurate network traffic. Specifically, TempoNet achieves a Domain Knowledge Check (DKC) violation rate statistically equivalent to that of observed real traffic, indicating adherence to valid network behaviors. Furthermore, TempoNet exhibits lower Jensen-Shannon Divergence (JSD) scores when analyzing categorical fields – including source IP address, destination IP address, destination port, and protocol – relative to real traffic. Lower JSD scores signify a closer probability distribution between generated and real traffic for these discrete variables, confirming realistic representation of network communication patterns.
Beyond the Simulation: Expanding the Boundaries of Network Resilience
TempoNet establishes a foundation for highly realistic network simulations within a Cyber Range environment, offering a critical space for both security training and proactive vulnerability assessment. This capability moves beyond theoretical exercises by generating network traffic that mirrors real-world conditions, allowing security professionals to hone their skills in a safe, controlled setting. Through these simulations, organizations can identify weaknesses in their systems before they are exploited by malicious actors, significantly bolstering their overall security posture. The resulting environment is not simply a testing ground, but a dynamic replica of operational networks, enabling thorough analysis of defenses against a spectrum of potential threats and providing valuable insights into system behavior under stress.
The synthetic network traffic produced by TempoNet serves as a critical resource for bolstering the performance of Intrusion Detection Systems (IDS). Traditional IDS development often relies on limited, real-world capture data, which may not encompass the breadth of modern network behaviors or effectively represent novel attack vectors. TempoNet addresses this limitation by generating diverse and realistic traffic patterns, allowing developers to thoroughly test IDS against a wider range of scenarios – from common exploits to zero-day threats. This rigorous testing process identifies vulnerabilities and weaknesses within the IDS, enabling targeted improvements to its detection accuracy and reducing false positive rates. Consequently, the enhanced IDS, trained with TempoNet’s synthetic data, exhibits increased resilience and effectiveness in safeguarding networks against evolving cyber threats, providing a more robust defense than systems reliant on static or insufficient training datasets.
TempoNet distinguishes itself from existing network traffic generation techniques by achieving a compelling equilibrium between several critical factors. While methods like Generative Adversarial Networks (GANs) and Bayesian Networks can model complex traffic patterns, they often suffer from high computational costs or limited diversity, hindering their practical application. Simpler approaches, such as NetShare, may offer efficiency but lack the fidelity to accurately represent real-world network behavior. TempoNet overcomes these limitations through its innovative architecture, delivering traffic that closely mirrors authentic network interactions while maintaining reasonable computational demands and a broad spectrum of representative scenarios. This unique combination positions TempoNet as a particularly effective tool for security testing, system validation, and the development of robust network defenses.
Researchers are extending TempoNet’s capabilities to model and generate network traffic specifically tailored to emulate a wide range of cyberattacks. This targeted approach moves beyond generic traffic simulation, allowing security professionals to proactively test defenses against realistic threat vectors – from distributed denial-of-service attacks and data exfiltration attempts to sophisticated ransomware deployments. By meticulously crafting traffic patterns that mirror the behaviors of actual malicious activity, the system enables more effective vulnerability assessments, refined intrusion detection signatures, and improved incident response strategies. The ultimate goal is to provide a dynamic and adaptable tool for security research and development, capable of anticipating and mitigating emerging threats in an ever-evolving digital landscape.
TempoNet’s approach to synthetic traffic generation isn’t about faithfully replicating existing patterns, but about understanding the underlying temporal dynamics that produce them. This resonates with a sentiment expressed by Edsger W. Dijkstra: “It’s not enough to understand the parts; you must understand how they fit together.” The model dissects network communication, not as a static entity, but as a process unfolding in time – a series of ‘ticks’ governed by point processes. By learning these timings alongside various network characteristics via multi-task learning, TempoNet effectively reverse-engineers the system, creating data that isn’t merely similar, but informed by the principles governing real-world network behavior. It’s a constructive dismantling, revealing the ‘click of truth’ within complex communication patterns.
Beyond the Simulation
TempoNet establishes a functional mimicry of network behavior, yet the truly interesting failures remain largely unexplored. The model excels at reproducing timing and communication patterns, but what systemic distortions arise when pushed beyond the boundaries of its training data? The next iteration shouldn’t focus on increased realism, but deliberate, controlled perturbation. Introduce anomalies not as deviations to detect, but as fundamental components of the generative process itself-a simulated evolution of attack vectors.
The multi-task learning aspect hints at a deeper principle: network security isn’t about identifying the ‘normal’, but quantifying the cost of deviation. Each successful intrusion isn’t a failure of detection, but a demonstration of an acceptable loss function. Future work should investigate TempoNet’s capacity to model this cost-to generate traffic not just like a compromised network, but optimized for undetected compromise.
Ultimately, the best hack is understanding why it worked, and every patch is a philosophical confession of imperfection. TempoNet provides a powerful tool for simulation, but the real challenge lies in building systems that anticipate-and even welcome-their own vulnerabilities.
Original article: https://arxiv.org/pdf/2601.15663.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- 39th Developer Notes: 2.5th Anniversary Update
- Gold Rate Forecast
- The 10 Most Beautiful Women in the World for 2026, According to the Golden Ratio
- TON PREDICTION. TON cryptocurrency
- Bitcoin’s Bizarre Ballet: Hyper’s $20M Gamble & Why Your Grandma Will Buy BTC (Spoiler: She Won’t)
- Celebs Who Fake Apologies After Getting Caught in Lies
- Nikki Glaser Explains Why She Cut ICE, Trump, and Brad Pitt Jokes From the Golden Globes
- Dividends: A Most Elegant Pursuit
- Venezuela’s Oil: A Cartography of Risk
- AI Stocks: A Slightly Less Terrifying Investment
2026-01-24 13:18